Tutorial
Updated
Original Nintendo Logo from Firmware (switch-logo-patcher)
Many have been able to patch their Nintendo boot logo with the logo of their choice: https://gbatemp.net/threads/custom-boot-logo-for-switch.569031/
In the instructions for the excellent Switch Logo Patcher, used in the thread above, it mentions the ability to reduce the size of the patches but to date, there are no instructions to do so.
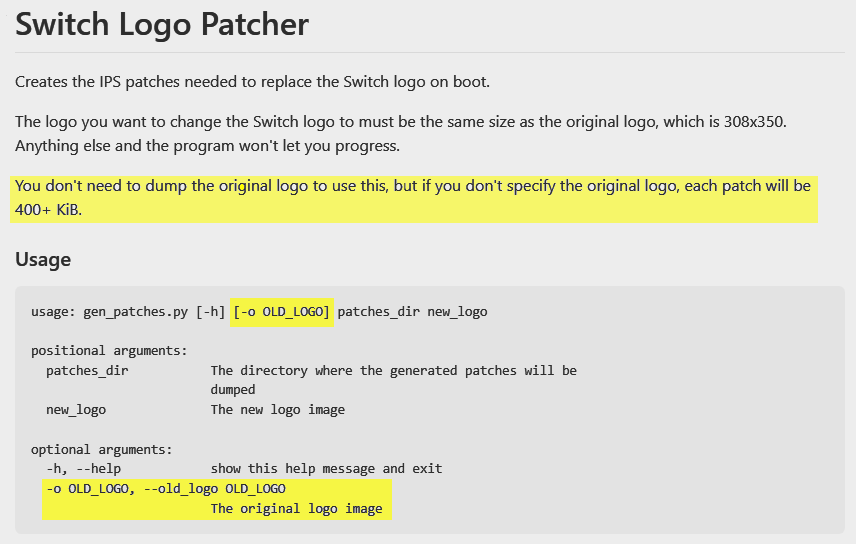
If you want to take advantage of the size reduction you will need to supply the Original Nintendo Logo from inside the firmware, but where is it and how do you extract it?
You might ask why nobody has simply copied the logo one time and shared it on this forum? The answer to that is here at GBATemp we don't believe in infringing upon the Intellectual Property rights of others. The Original Nintendo Logo belongs to Nintendo and is thus not to be shared here or on any other public forum.
The following is an abbreviated version of my journey to be able to extract the logo from a copy of the Firmware included on my Switch. I won't be including the Firmware here because it too, is the IP of Nintendo.
Thanks to the folks at #ReSwitched
friedkeenan (SLP Dev), Behemoth, shchmue, SciresM, Retroid, TSR Berry for tolerating my n00bness and walking me through everything!
Thanks to @impeeza for providing some better methods here.
Down the rabbit hole we go...

In the instructions for the excellent Switch Logo Patcher, used in the thread above, it mentions the ability to reduce the size of the patches but to date, there are no instructions to do so.
If you want to take advantage of the size reduction you will need to supply the Original Nintendo Logo from inside the firmware, but where is it and how do you extract it?
You might ask why nobody has simply copied the logo one time and shared it on this forum? The answer to that is here at GBATemp we don't believe in infringing upon the Intellectual Property rights of others. The Original Nintendo Logo belongs to Nintendo and is thus not to be shared here or on any other public forum.
The following is an abbreviated version of my journey to be able to extract the logo from a copy of the Firmware included on my Switch. I won't be including the Firmware here because it too, is the IP of Nintendo.
Thanks to the folks at #ReSwitched
friedkeenan (SLP Dev), Behemoth, shchmue, SciresM, Retroid, TSR Berry for tolerating my n00bness and walking me through everything!
Thanks to @impeeza for providing some better methods here.
Down the rabbit hole we go...
- Download the following tools, unzip them and place them in your Windows path (or simply install it in the case of HxD and Gimp2):
hactool (if you get a segfault or nothing happens when you run hactool, others have noted it too and the recommendation is to compile it yourself...which I've done here. Always scan for viruses!)hactoolnet
HxD (any hex editor will do. I happen to use this one.)
Gimp 2 (needed for importing raw RGBA data and converting it to PNG) - Procure a copy of your prod.keys from your Switch using Lockpick_RCM and copy them to your PC (preferably placed in %HOMEDRIVE%%HOMEPATH%\.switch\prod.keys as this is where most tools expect to see them)
- Procure a copy of FW that matches the version on your Switch. There are other tutorials that show how to extract your own Firmware such as this one using Goldleaf.
- With the FW zip file in hand create a working directory and unzip your copy into it. You will see a huge list of .nca files like this:
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>dir
Volume in drive C has no label.
Volume Serial Number is 4AF0-ADF0
Directory of C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1
05/30/2022 05:27 PM <DIR> .
05/30/2022 05:27 PM <DIR> ..
04/19/2022 11:44 AM 713,216 02259fd41066eddbc64e0fdd217d9d2f.nca
04/19/2022 11:44 AM 793,600 02582a2cd46cc226ce72c8a52504cd97.nca
04/19/2022 11:46 AM 3,837,440 02b1dd519a6df4de1b11871851d328a1.nca
04/19/2022 11:45 AM 3,278,336 0319d27ebdc4f4556b0ca948e2ccc081.nca
04/19/2022 11:47 AM 497,152 0450e376470f98b8a8a065787cfa410a.nca
...
04/19/2022 11:45 AM 179,712 fbefa4e085899a70195c3ed215778805.nca
04/19/2022 11:44 AM 5,632 fc565db2a1e9aabbb0547c8d82b16df5.cnmt.nca
04/19/2022 11:45 AM 854,528 fce10ab27f4646b2ef9c8e1b13aba21e.nca
04/19/2022 11:47 AM 576,512 fd0d23003ea5602c24ac4e41101c16fd.nca
225 File(s) 336,152,576 bytes
2 Dir(s) 35,121,111,040 bytes free
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>
- Head over to https://switchbrew.org/wiki/Title_list and look for the VI module (this is the module that contains the logo) and take note of its TitleID (010000000000002D)
- Use hacktoolnet in your working directory to find the .nca that contains the TitleID we want
Code:hactoolnet -t switchfs --listncas . | findstr.exe 010000000000002D
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>hactoolnet -t switchfs --listncas . | findstr.exe 010000000000002D
0da31addb3dc04f4cb27a6125803a0ce Program 010000000000002D
d18c9c05c4a001486cdf05fcbbd08abc Meta 010000000000002D
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>
- Extract the one that says Program next in the middle column using hactool
Code:hactool -t nca --exefsdir 0da31addb3dc04f4cb27a6125803a0ce.nca_out 0da31addb3dc04f4cb27a6125803a0ce.nca
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>hactool -t nca --exefsdir 0da31addb3dc04f4cb27a6125803a0ce.nca_out 0da31addb3dc04f4cb27a6125803a0ce.nca
[WARN] prod.keys does not exist.
NCA:
Magic: NCA3
Fixed-Key Index: 0x0
Fixed-Key Signature: 165EAA0015347673906A3D363162993E5744E36A359C5B0D61FF475E47F4D663
B2BF74447BEADEC43F8CEFD6FA1B2063B599E09CB1C4BA537DA429BE931CC430
94CCB65CB4C5B31258CA56F4F9B6C4F87D8F88A09A094D7CD57B7BF089A4F9CF
0A087F17B4D8B398B9CFF51311A6D2E3936C2002B545DFEAF360F12F638B56EF
47A30E3C7136BD9BF1D1C9832FE398307C4DCD9691E26D30BE5D5219B6FEFC96
DF50E757311875A9DF49B464BAD5C5B0CA6A961171A43E7B58B6786242A9F9B6
2918EA760BFC3C217899983640F80BB2B2253557B44C8EE379AE465B791AC6B7
F2B57BDE0A3A1F87C19D8464150889D45487D6C3B3A0BDEDE1A9166698E554F0
NPDM Signature: 41153F64AD2FACD4B027C38703F208E4F8C54350593A0AA57478686020354352
1B578F4CB1F3E158679B74EDC01156541C528FDFA864B1EAA7F43224C7DB15A8
2F0D66256204A1C6118204E3CEB15743C483D03E20763206B3B33CF44F853D39
6C7B7B6501C7FF3818BA213108D3945E0795C62C1ECCAD14B42E2F360A626FBB
84BE13AEC587A75F59BAEA4A25144225BE7E57212FC4B31A785E2B7F8E2AB057
9C5BF0030E10EDA52B9D7E701F461D1DDEA744798CF5C8437624C90E5738A4AA
04517DB677D893B101CC1285998FB0ADACC40ED0378FD85CBB77EFADAD4B90A3
BE93AEEA8094A81A9221B1952CB6A53E6D77D0F6335344B873D389012246C5F4
Content Size: 0x0000000f5e00
Title ID: 010000000000002d
SDK Version: 14.3.0.0
Distribution type: Download
Content Type: Program
Master Key Revision: 0xD (Unknown)
Encryption Type: Standard crypto
Key Area Encryption Key: 0
Key Area (Encrypted):
Key 0 (Encrypted): CD774824AA7210E7412AB7E848238A50
Key 1 (Encrypted): CD774824AA7210E7412AB7E848238A50
Key 2 (Encrypted): 5F8EE156313D8AE9FD40A2273ADFD5D3
Key 3 (Encrypted): CD774824AA7210E7412AB7E848238A50
Key Area (Decrypted):
Key 0 (Decrypted): 00000000000000000000000000000000
Key 1 (Decrypted): 00000000000000000000000000000000
Key 2 (Decrypted): CEC07FAF5BD22C6C390B7C1F8E71766B
Key 3 (Decrypted): 00000000000000000000000000000000
NPDM:
Magic: META
MMU Flags: 27
Main Thread Priority: 16
Default CPU ID: 3
Version: 14.0.0-1024 (939525120)
Main Thread Stack Size: 0x4000
Title Name: vi
ACID:
Magic: ACID
Signature Key: 0
Signature: 539381816FD29FD0731C0A00039493098B30C2078A495CD241721216C4EA20DA
4D842EE70C1FCA79D25F45E62D4854E61914878CC4735677DD801CE30896DE32
31DD95EF9D687019F6CD211CEDA4F1E02AF260F75BBB5B1A243576873E4AA7AE
4ABACF5A36C2377BC1E356DEC9502532081AF7FD5B82C8B772E77C2427715326
71CA65322C10A6DC0730296AC8E29BB082E9680358622B499F34B18B179AB838
3CF29B2AF71D0E7CE9884B98465928E2B65DDE329C5FA1FA01E69134562DF6CC
ED0D15543348E260EEBAD5CA95095E754A46833EDDA6ACD18E95A57105FFFFD3
880107E999A0CADF08A5B494FCDE2A551F9BB7E1A2C338496F301E4CF5E8ED99
Header Modulus: F76903B8C7D858FFBC4DED8C59AF2A04327BB243D90FBB2B0EAD4D5DDF61C2A8
E24837564228D73545D101A7F8A8854EB94D4D68AC39D9F9CF274CAA8E9198D8
69EB6AED54C09ED7FFC191C5A0068BA667F1B7400F7C7020904E910434899D2A
7D92474A5AEE891E6F15E2F57916B3EE2D552E5627BD1F974F2FD3AAB35B1D5A
8B291A6B1C3222246C4182D20E9C792252B2F2B5CB242407235DEC103051059B
805AF5971EDEF931EEFB5548F7E1844DEC33BAB6EDB9EF34229E47622F3B111F
6809F2BFE4E856AF31D542BB35034F67BCCEB8558E48311E56D481E371FAA519
0FE5A60C4070261E24BDF1D3B708C4D5156689BBEDD6AB0811E3F234263AA58D
Is Retail: 1
Pool Partition: 3
Title ID Range: 010000000000002d-010000000000002d
ACI0:
Magic: ACI0
Title ID: 010000000000002d
Kernel Access Control:
Lowest Allowed Priority: 4
Highest Allowed Priority: 63
Lowest Allowed CPU ID: 3
Highest Allowed CPU ID: 3
Allowed SVCs: svcSetHeapSize (0x01)
svcSetMemoryPermission (0x02)
svcSetMemoryAttribute (0x03)
svcMapMemory (0x04)
svcUnmapMemory (0x05)
svcQueryMemory (0x06)
svcExitProcess (0x07)
svcCreateThread (0x08)
svcStartThread (0x09)
svcExitThread (0x0a)
svcSleepThread (0x0b)
svcGetThreadPriority (0x0c)
svcSetThreadPriority (0x0d)
svcGetThreadCoreMask (0x0e)
svcSetThreadCoreMask (0x0f)
svcGetCurrentProcessorNumber (0x10)
svcSignalEvent (0x11)
svcClearEvent (0x12)
svcMapSharedMemory (0x13)
svcUnmapSharedMemory (0x14)
svcCreateTransferMemory (0x15)
svcCloseHandle (0x16)
svcResetSignal (0x17)
svcWaitSynchronization (0x18)
svcCancelSynchronization (0x19)
svcArbitrateLock (0x1a)
svcArbitrateUnlock (0x1b)
svcWaitProcessWideKeyAtomic (0x1c)
svcSignalProcessWideKey (0x1d)
svcGetSystemTick (0x1e)
svcConnectToNamedPort (0x1f)
svcSendSyncRequestLight (0x20)
svcSendSyncRequest (0x21)
svcSendSyncRequestWithUserBuffer (0x22)
svcSendAsyncRequestWithUserBuffer (0x23)
svcGetProcessId (0x24)
svcGetThreadId (0x25)
svcBreak (0x26)
svcOutputDebugString (0x27)
svcReturnFromException (0x28)
svcGetInfo (0x29)
svcWaitForAddress (0x34)
svcSignalToAddress (0x35)
svcCreateSession (0x40)
svcAcceptSession (0x41)
svcReplyAndReceiveLight (0x42)
svcReplyAndReceive (0x43)
svcReplyAndReceiveWithUserBuffer (0x44)
svcCreateEvent (0x45)
svcMapTransferMemory (0x51)
svcUnmapTransferMemory (0x52)
Handle Table Size: 192
Minimum Kernel Version: 145
Service Access Control:
Hosts: caps:sc
caps:ss
cec-mgr
lbl
mm:u
vi:m
vi:s
vi:u
Accesses: caps:c
dispdrv
erpt:c
fatal:u
fgm:9
fsp-srv
gpio
i2c
lm
nvdrv:s
ovln:snd
psc:m
pwm
set:sys
Filesystem Access Control:
Version: 1
Raw Permissions: 0x0000000000100000
RW Permissions: MountContent_System
Boolean Permissions:
Sections:
Section 0:
Offset: 0x000000000c00
Size: 0x0000000f5200
Partition Type: ExeFS
Section CTR: 000000010000000000000000000000C0
Superblock Hash: 0FDA3A413300BAA75E3899F8456259D27D6517973D08E98EC16DD00ED0A93008
Hash Table:
Offset: 000000000000
Size: 000000000f60
Block Size: 0x2000
PFS0 Offset: 000000000f60
PFS0 Size: 0000000f4141
Saving main to 0da31addb3dc04f4cb27a6125803a0ce.nca_out/main...
Saving main.npdm to 0da31addb3dc04f4cb27a6125803a0ce.nca_out/main.npdm...
Done!
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>
- Change to the new directory that was just created and you will see two new files.
Code:cd 0da31addb3dc04f4cb27a6125803a0ce.nca_out
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1>cd 0da31addb3dc04f4cb27a6125803a0ce.nca_out
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1\0da31addb3dc04f4cb27a6125803a0ce.nca_out>dir
Volume in drive C has no label.
Volume Serial Number is 4AF0-ADF0
Directory of C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1\0da31addb3dc04f4cb27a6125803a0ce.nca_out
05/30/2022 08:03 PM <DIR> .
05/30/2022 08:03 PM <DIR> ..
05/30/2022 08:06 PM 998,453 main
05/30/2022 08:06 PM 1,196 main.npdm
2 File(s) 999,649 bytes
2 Dir(s) 32,256,425,984 bytes free
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1\0da31addb3dc04f4cb27a6125803a0ce.nca_out>
- We're interested in the almost 1G main file but it's currently lz4 compressed so to fix that we need to run hactool again.
Code:hactool --uncompressed=main_uncompressed -t nso0 main
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1\0da31addb3dc04f4cb27a6125803a0ce.nca_out>hactool --uncompressed=main_uncompressed -t nso0 main
[WARN] prod.keys does not exist.
NSO0:
Build Id: AFEAACF3E88AB539574689D1458060657E81E088000000000000000000000000
Sections:
.text: 00000000-00122000
.rodata: 00122000-0019a000
.rwdata: 0019a000-01bf12e8
.bss: 01bf12e8-0220b000
Done!
C:\Users\wwiii\Downloads\switch\firmware\Firmware 14.1.1\0da31addb3dc04f4cb27a6125803a0ce.nca_out>
NOTE: take a look at the Build Id: in the results of that command and you will see that it matches the has in the original code here. Neat, huh?
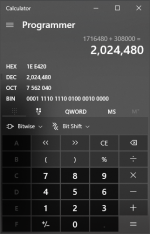
- Aside from knowing you're on the right track, you will also see another number (called an offset) to the right of the hash: 1716480
UPDATE: @impeeza has a fresh take on how to derive the necessary offsets for any Firmware without depending upon the code reference above.
On step 10: You don't need the calculator; on HxD you can press CTRL+G and put the offset on decimal value and get on the Hex Offset:
I wish to know how to find the offset without looking on the script of the project https://github.com/friedkeenan/switch-logo-patcher/blob/master/gen_patches.py.
I do this guide on several firmwares from 8 to 14 and searching forward for 00 00 00 FF 00 00 00 FF from start of main_uncompressed file found the beginning of the data:
And finding Backward the same string from the end of file get the last offset:
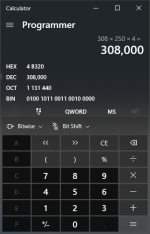
We will want to know what that is in Hex so open up your calculator (yes, THAT calculator) and put it in Programmer mode by clicking the hamburger (the three horizontal lines in the upper left-hand corner). Now click DEC (for Decimal) and enter the offset from above and note that it automatically converts to HEX for you! Neat, huh?
- Open up the freshly uncompressed main_uncompressed file with HxD or your hex editor of choice and scroll down to the offset highlighted in yellow above: 1A3100
@impeeza has provided another clever tip in his post.
you can use the Select Block command (CTRL+E):
on that dialog, you can specify the start of the block and the length or the end of the same.
You will know you're in the right place when you see sets of four numbers in the pattern of (R)ed, (G)reen, (B)lue and (A)lpha Channel. This is what's known as raw or RGBA.
- Highlight the beginning at 1A3100 and then just scroll down until you reach the end of the pattern. In our case it happens to be 0x20C55F where the pattern stops with repeating zeros (0).
@impeeza points out that you can derive the last offset by the size of the graphic (308 * 350 * 4 = 431,200 or 0x69460). You can simply add the size of the graphic to your first offset to get the last offset without guessing!
- Click <Edit><Copy> (or Ctrl+C) to copy all of that, got to <File><New> (or Ctrl+N) to open a new file then hit <Edit><Paste> (or Ctrl+V) to paste the values in the new file.
- Save the file as original.data by clicking <File><Save As> (there is no shortcut for this).
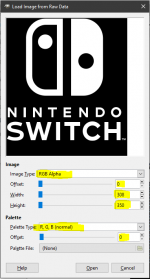
- Wake up the Gimp (2)and open your original.data file that you just saved.
- Since it is just raw RGBA data it doesn't know how to represent it yet so when you click open it will pop up another dialog where you will need to make sure to change the highlighted value below to match.
- Click <Open> one more time and your Original Nintendo Logo will be in focus and ready for the final manipulation!
- In Gimp, hit <File><Export As> (or Shift+Ctrl+E) . This time change the Name to be original.png and the file type to be PNG image (*.png) and then click <Export>.
- In the export dialog I only changed the compression to 0 and then clicked <Export>.
- The only thing left to do is to copy your original.png file to your switch-logo-patcher directory and finally run the full command!
Code:python gen_patches.py -o original.png nintendont nintendont.png
C:\Users\wwiii\Downloads\switch\switch-logo-patcher\nintendont.good>dir
Volume in drive C has no label.
Volume Serial Number is 4AF0-ADF0
Directory of C:\Users\wwiii\Downloads\switch\switch-logo-patcher\nintendont.good
03/27/2022 03:08 PM <DIR> .
03/27/2022 03:08 PM <DIR> ..
03/27/2022 03:08 PM 431,243 01890C643E9D6E17B2CDA77A9749ECB9A4F676D6.ips
03/27/2022 03:08 PM 431,243 0767302E1881700608344A3859BC57013150A375.ips
03/27/2022 03:08 PM 431,243 3EC573CB22744A993DFE281701E9CBFE66C03ABD.ips
03/27/2022 03:08 PM 431,243 65A23B52FCF971400CAA4198656D73867D7F1F1D.ips
03/27/2022 03:08 PM 431,243 723DF02F6955D903DF7134105A16D48F06012DB1.ips
03/27/2022 03:08 PM 431,243 7421EC6021AC73DD60A635BC2B3AD6FCAE2A6481.ips
03/27/2022 03:08 PM 431,243 7B4123290DE2A6F52DE4AB72BEA1A83D11214C71.ips
03/27/2022 03:08 PM 431,243 7C5894688EDA24907BC9CE7013630F365B366E4A.ips
03/27/2022 03:08 PM 431,243 82EE58BEAB54C1A9D4B3D9ED414E84E31502FAC6.ips
03/27/2022 03:08 PM 431,243 96529C3226BEE906EE651754C33FE3E24ECAE832.ips
03/27/2022 03:08 PM 431,243 967F4C3DFC7B165E4F7981373EC1798ACA234A45.ips
03/27/2022 03:08 PM 431,243 98446A07BC664573F1578F3745C928D05AB73349.ips
03/27/2022 03:08 PM 431,243 AFEAACF3E88AB539574689D1458060657E81E088.ips
03/27/2022 03:08 PM 431,243 B295D3A8F8ACF88CB0C5CE7C0488CC5511B9C389.ips
03/27/2022 03:08 PM 431,243 C088ADC91417EBAE6ADBDF3E47946858CAFE1A82.ips
03/27/2022 03:08 PM 431,243 C79F22F18169FCD3B3698A881394F6240385CDB1.ips
03/27/2022 03:08 PM 431,243 D689E9FAE7CAA4EC30B0CD9B419779F73ED3F88B.ips
17 File(s) 7,331,131 bytes
2 Dir(s) 32,216,248,320 bytes free
C:\Users\wwiii\Downloads\switch\switch-logo-patcher\nintendont.good>cd ..\nintendont
C:\Users\wwiii\Downloads\switch\switch-logo-patcher\nintendont>dir
Volume in drive C has no label.
Volume Serial Number is 4AF0-ADF0
Directory of C:\Users\wwiii\Downloads\switch\switch-logo-patcher\nintendont
05/30/2022 10:26 PM <DIR> .
05/30/2022 10:26 PM <DIR> ..
05/30/2022 10:26 PM 119,563 01890C643E9D6E17B2CDA77A9749ECB9A4F676D6.ips
05/30/2022 10:26 PM 119,563 0767302E1881700608344A3859BC57013150A375.ips
05/30/2022 10:26 PM 119,563 3EC573CB22744A993DFE281701E9CBFE66C03ABD.ips
05/30/2022 10:26 PM 119,563 65A23B52FCF971400CAA4198656D73867D7F1F1D.ips
05/30/2022 10:26 PM 119,563 723DF02F6955D903DF7134105A16D48F06012DB1.ips
05/30/2022 10:26 PM 119,563 7421EC6021AC73DD60A635BC2B3AD6FCAE2A6481.ips
05/30/2022 10:26 PM 119,563 7B4123290DE2A6F52DE4AB72BEA1A83D11214C71.ips
05/30/2022 10:26 PM 119,563 7C5894688EDA24907BC9CE7013630F365B366E4A.ips
05/30/2022 10:26 PM 119,563 82EE58BEAB54C1A9D4B3D9ED414E84E31502FAC6.ips
05/30/2022 10:26 PM 119,563 96529C3226BEE906EE651754C33FE3E24ECAE832.ips
05/30/2022 10:26 PM 119,563 967F4C3DFC7B165E4F7981373EC1798ACA234A45.ips
05/30/2022 10:26 PM 119,563 98446A07BC664573F1578F3745C928D05AB73349.ips
05/30/2022 10:26 PM 119,563 AFEAACF3E88AB539574689D1458060657E81E088.ips
05/30/2022 10:26 PM 119,563 B295D3A8F8ACF88CB0C5CE7C0488CC5511B9C389.ips
05/30/2022 10:26 PM 119,563 C088ADC91417EBAE6ADBDF3E47946858CAFE1A82.ips
05/30/2022 10:26 PM 119,563 C79F22F18169FCD3B3698A881394F6240385CDB1.ips
05/30/2022 10:26 PM 119,563 D689E9FAE7CAA4EC30B0CD9B419779F73ED3F88B.ips
17 File(s) 2,032,571 bytes
2 Dir(s) 32,215,785,472 bytes free
C:\Users\wwiii\Downloads\switch\switch-logo-patcher\nintendont>
- As you can see the new ips patch files are about 25-30% of the previously known good ips patches! Copy the entire patch directory to /atmosphere/exefs_patches/. (If you have an old set of the old patches be sure to remove the directory first.)
- Reboot your switch and enjoy your new lightweight patched logo!
Attachments
Last edited by binkinator,








 you may have a PATH environment problem, if the command pip says
you may have a PATH environment problem, if the command pip says