You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Staff Posts
Recent threadmarks
sharing files
Important Posts
Recent threadmarks
Firmwaresnot public yet.Wow
Is Android OLED public already?
also firmware includes Auto-HOS-off, but Android did reboot instead - strange
Let's call it now the switchroot modchip.
Thank you @rehius to bring us this.
Can't wait to finish my switch lite whit this.
Thank you @rehius to bring us this.
Can't wait to finish my switch lite whit this.
This might be a dumb question, but to me, logically, why don't we just use the uf2 we currently have and just overwrite it with the working one, then resale the uf2 after the fact?
I assume there I'd a technical reason why yhag won't actually work
I assume there I'd a technical reason why yhag won't actually work
uanyone know?
is that cpu mos
didnt solder the mosfet ?anyone know?
is that cpu mosfet
it goes to hos directly
it does, that thing right below sd cardu
didnt solder the mosfet ?
Either use a mosfet on cpu caps or get the ribbonit does, that thing right below sd card
yes i saw it, cant boot to hekate?it does, that thing right below sd card
CYAN = no glitch reactionanyone know?
is that cpu mosfet
it goes to hos directly
MOSFET must be connected very close, very thick wire, or direct solder
on video - very very long very very thin wire. cannot do 20 Amperes
Okay, after taking some time off I decided to look at this again and realized that they're most definitely fingerprinting (or rather, changing behaviour) based on the flash ID. They call flash_get_unique_id as part of an init callback (I thought this was some random flash func) and then continuously copy the unique ID: (lol I initially missed that mov R2, R4)
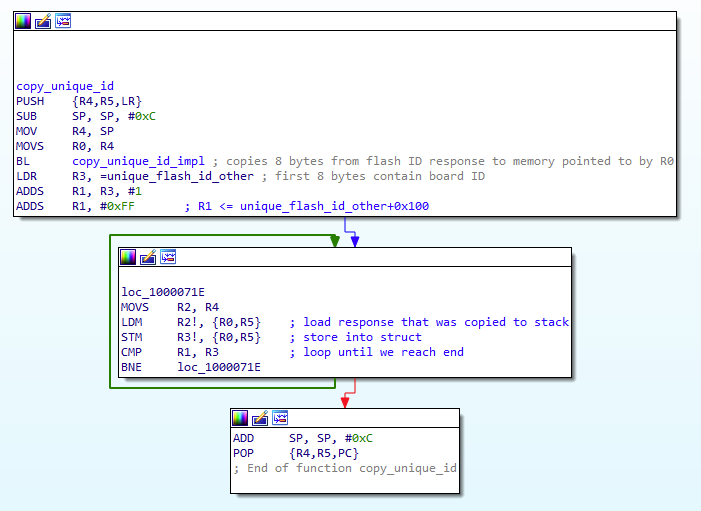
Based on this data it writes to memory in a specific pattern which is much more complicated to patch out than a simple check; the easiest way to go about this would be if someone dumped a firmware and a unique ID and then emulated it instruction-by-instruction. At the very least it would be helpful to see what they're doing with the 0x110B0 bytes copied from 0x1000297C to the SRAM base (0x20000000). The only problem I see from this would maybe be navigating the function that looks for the sequence on the CMD pin.
I also realized that they probably exit the XIP flash because it runs off of clk_sys which they're changing, because otherwise the dumped firmware.bin would look strange and I don't think the flash would be able to keep up anyways.
For reference, the initially dumped firmware grabs the unique ID in the init routine at 0x10002608, which gets copied into a 256-byte structure at 0x20025868 in the routine at 0x1000070C. Interestingly, the other .uf2s posted here do something slightly different when copying the unique ID, for some reason.
Other than this, I'm basically stuck until someone does what I suggested or if it turns out that binary blob has easy-to-disassemble ARM code.
Based on this data it writes to memory in a specific pattern which is much more complicated to patch out than a simple check; the easiest way to go about this would be if someone dumped a firmware and a unique ID and then emulated it instruction-by-instruction. At the very least it would be helpful to see what they're doing with the 0x110B0 bytes copied from 0x1000297C to the SRAM base (0x20000000). The only problem I see from this would maybe be navigating the function that looks for the sequence on the CMD pin.
I also realized that they probably exit the XIP flash because it runs off of clk_sys which they're changing, because otherwise the dumped firmware.bin would look strange and I don't think the flash would be able to keep up anyways.
For reference, the initially dumped firmware grabs the unique ID in the init routine at 0x10002608, which gets copied into a 256-byte structure at 0x20025868 in the routine at 0x1000070C. Interestingly, the other .uf2s posted here do something slightly different when copying the unique ID, for some reason.
Other than this, I'm basically stuck until someone does what I suggested or if it turns out that binary blob has easy-to-disassemble ARM code.
0.15-0.2mm diameter okare the 0.7mm cables for rp2040 soldering ok?
If you look at the amount of power you are going to use, you can calculate the wire thickness. For this application you don't need anything more than 25 AWG (0.45mm) - that's more than thick enough, so the 0.7mm wire you are using is fine.are the 0.7mm cables for rp2040 soldering ok?
For anyone wanting to reverse engineering this, the focus needs to be on getting both a dump and the unique id of the same working chip. Adding a check to verify the unique id is kindergarten stuff, they wouldn't do that. At minimum they would encrypt the rest of the information using the unique id as a key or part of the key.Okay, after taking some time off I decided to look at this again and realized that they're most definitely fingerprinting (or rather, changing behaviour) based on the flash ID. They call flash_get_unique_id as part of an init callback (I thought this was some random flash func) and then continuously copy the unique ID: (lol I initially missed that mov R2, R4)
View attachment 357376
Based on this data it writes to memory in a specific pattern which is much more complicated to patch out than a simple check; the easiest way to go about this would be if someone dumped a firmware and a unique ID and then emulated it instruction-by-instruction. At the very least it would be helpful to see what they're doing with the 0x110B0 bytes copied from 0x1000297C to the SRAM base (0x20000000). The only problem I see from this would maybe be navigating the function that looks for the sequence on the CMD pin.
I also realized that they probably exit the XIP flash because it runs off of clk_sys which they're changing, because otherwise the dumped firmware.bin would look strange and I don't think the flash would be able to keep up anyways.
For reference, the initially dumped firmware grabs the unique ID in the init routine at 0x10002608, which gets copied into a 256-byte structure at 0x20025868 in the routine at 0x1000070C. Interestingly, the other .uf2s posted here do something slightly different when copying the unique ID, for some reason.
Other than this, I'm basically stuck until someone does what I suggested or if it turns out that binary blob has easy-to-disassemble ARM code.
Page 40For anyone wanting to reverse engineering this, the focus needs to be on getting both a dump and the unique id of the same working chip. Adding a check to verify the unique id is kindergarten stuff, they wouldn't do that. At minimum they would encrypt the rest of the information using the unique id as a key or part of the key.
hello guys, there is a problem, after breaking the capacitor at 3.3 v, I got a blue screen error, I hope it's from the capacitor, because at the same time, it short-circuited the 2 cables I connected the mosfet, so I hope tegra x1 is not broken.
View attachment 357480
hello guys, there is a problem, after breaking the capacitor at 3.3 v, I got a blue screen error, I hope it's from the capacitor, because at the same time, it short-circuited the 2 cables I connected the mosfet, so I hope tegra x1 is not broken.
Dont ask that questions here its for the picofly
Similar threads
- Replies
- 3
- Views
- 1K
- Replies
- 2
- Views
- 358
- Replies
- 42
- Views
- 6K
Site & Scene News
New Hot Discussed
-
-
24K views
Wii U and 3DS online services shutting down today, but Pretendo is here to save the day
Today, April 8th, 2024, at 4PM PT, marks the day in which Nintendo permanently ends support for both the 3DS and the Wii U online services, which include co-op play...by ShadowOne333 179 -
19K views
Nintendo Switch firmware update 18.0.1 has been released
A new Nintendo Switch firmware update is here. System software version 18.0.1 has been released. This update offers the typical stability features as all other... -
17K views
The first retro emulator hits Apple's App Store, but you should probably avoid it
With Apple having recently updated their guidelines for the App Store, iOS users have been left to speculate on specific wording and whether retro emulators as we... -
16K views
Delta emulator now available on the App Store for iOS
The time has finally come, and after many, many years (if not decades) of Apple users having to side load emulator apps into their iOS devices through unofficial...by ShadowOne333 96 -
15K views
MisterFPGA has been updated to include an official release for its Nintendo 64 core
The highly popular and accurate FPGA hardware, MisterFGPA, has received today a brand new update with a long-awaited feature, or rather, a new core for hardcore...by ShadowOne333 54 -
13K views
TheFloW releases new PPPwn kernel exploit for PS4, works on firmware 11.00
TheFlow has done it again--a new kernel exploit has been released for PlayStation 4 consoles. This latest exploit is called PPPwn, and works on PlayStation 4 systems... -
12K views
Nintendo takes down Gmod content from Steam's Workshop
Nintendo might just as well be a law firm more than a videogame company at this point in time, since they have yet again issued their now almost trademarked usual...by ShadowOne333 113 -
11K views
A prototype of the original "The Legend of Zelda" for NES has been found and preserved
Another video game prototype has been found and preserved, and this time, it's none other than the game that spawned an entire franchise beloved by many, the very...by ShadowOne333 31 -
9K views
Anbernic reveals specs details of pocket-sized RG28XX retro handheld
Anbernic is back with yet another retro handheld device. The upcoming RG28XX is another console sporting the quad-core H700 chip of the company's recent RG35XX 2024... -
9K views
Nintendo "Indie World" stream announced for April 17th, 2024
Nintendo has recently announced through their social media accounts that a new Indie World stream will be airing tomorrow, scheduled for April 17th, 2024 at 7 a.m. PT...by ShadowOne333 53
-
-
-
179 replies
Wii U and 3DS online services shutting down today, but Pretendo is here to save the day
Today, April 8th, 2024, at 4PM PT, marks the day in which Nintendo permanently ends support for both the 3DS and the Wii U online services, which include co-op play...by ShadowOne333 -
113 replies
Nintendo takes down Gmod content from Steam's Workshop
Nintendo might just as well be a law firm more than a videogame company at this point in time, since they have yet again issued their now almost trademarked usual...by ShadowOne333 -
97 replies
The first retro emulator hits Apple's App Store, but you should probably avoid it
With Apple having recently updated their guidelines for the App Store, iOS users have been left to speculate on specific wording and whether retro emulators as we...by Scarlet -
96 replies
Delta emulator now available on the App Store for iOS
The time has finally come, and after many, many years (if not decades) of Apple users having to side load emulator apps into their iOS devices through unofficial...by ShadowOne333 -
79 replies
Nintendo Switch firmware update 18.0.1 has been released
A new Nintendo Switch firmware update is here. System software version 18.0.1 has been released. This update offers the typical stability features as all other...by Chary -
77 replies
TheFloW releases new PPPwn kernel exploit for PS4, works on firmware 11.00
TheFlow has done it again--a new kernel exploit has been released for PlayStation 4 consoles. This latest exploit is called PPPwn, and works on PlayStation 4 systems...by Chary -
55 replies
Nintendo Switch Online adds two more Nintendo 64 titles to its classic library
Two classic titles join the Nintendo Switch Online Expansion Pack game lineup. Available starting April 24th will be the motorcycle racing game Extreme G and another...by Chary -
54 replies
MisterFPGA has been updated to include an official release for its Nintendo 64 core
The highly popular and accurate FPGA hardware, MisterFGPA, has received today a brand new update with a long-awaited feature, or rather, a new core for hardcore...by ShadowOne333 -
53 replies
Nintendo "Indie World" stream announced for April 17th, 2024
Nintendo has recently announced through their social media accounts that a new Indie World stream will be airing tomorrow, scheduled for April 17th, 2024 at 7 a.m. PT...by ShadowOne333 -
52 replies
The FCC has voted to restore net neutrality, reversing ruling from 2017
In 2017, the United States Federal Communications Commission (FCC) repealed net neutrality. At the time, it was a major controversy between internet service providers...by Chary
-
Popular threads in this forum
General chit-chat
- No one is chatting at the moment.
-
 @
Psionic Roshambo:
I wonder if they could get CPUs to run that hot then use the heat to power a steam turbine to power the CPUs....
@
Psionic Roshambo:
I wonder if they could get CPUs to run that hot then use the heat to power a steam turbine to power the CPUs.... -
-
 @
Psionic Roshambo:
It's not the movies or games downloads that I would worry about, like breaking into networks, downloading encrypted things, spying on network traffic. I have seen so many "Top Secret" seals on files when I was a kid
@
Psionic Roshambo:
It's not the movies or games downloads that I would worry about, like breaking into networks, downloading encrypted things, spying on network traffic. I have seen so many "Top Secret" seals on files when I was a kid -
 @
Psionic Roshambo:
I was obsessed with finding UFOs, a surprising amount of US files where stashed on computers in other countries, China back in the early 90s omg sooo much
@
Psionic Roshambo:
I was obsessed with finding UFOs, a surprising amount of US files where stashed on computers in other countries, China back in the early 90s omg sooo much -
 @
BigOnYa:
Yea that crazy, I've never tried hack into anything, I just pirate, and my ISP have send me 3-4 letters, so had to VPN it
@
BigOnYa:
Yea that crazy, I've never tried hack into anything, I just pirate, and my ISP have send me 3-4 letters, so had to VPN it -
 @
Psionic Roshambo:
Ship to ship communication software for the Navy although without access to the encrypting chips it was mostly useless
@
Psionic Roshambo:
Ship to ship communication software for the Navy although without access to the encrypting chips it was mostly useless -
 @
Psionic Roshambo:
I bet now a 4090 could probably crack it? Hmmm maybe not even back then I'm pretty sure they where using like 1024 bit encryption
@
Psionic Roshambo:
I bet now a 4090 could probably crack it? Hmmm maybe not even back then I'm pretty sure they where using like 1024 bit encryption -
-
-
-
-
-
-
-
-
-
 @
Psionic Roshambo:
I remember one time I downloaded like a 500MB ISO file on 56K and that literally took like 2 days
@
Psionic Roshambo:
I remember one time I downloaded like a 500MB ISO file on 56K and that literally took like 2 days -
-
-
-
-
-
-
-







