Has anyone thought about uncovering the system encryption's private key by performing a memory dump? The private key has to exist in the system's memory at some point, if it's being used. A memdump will allow the privkey to be accessed while encrypted.
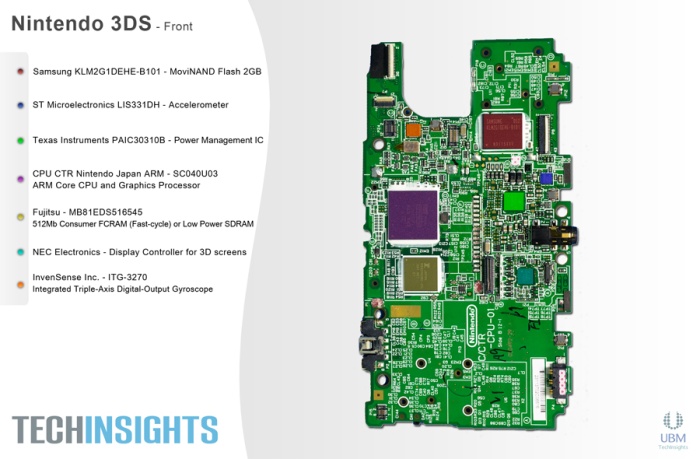
The original RAM chip can be removed and a reversed engineered version of the chip that allows interface with a PC can be attached in it's place. After connecting the modified RAM chip to a PC, we can scan system memory until we find the key.
Once you have they key, you'll be able to run any code you want on the system. The storage NAND is a separate chip on the PCB, so replacing the RAM shouldn't effect it. This seems like a possible method to hack the system.
Anyone thought about trying?

The original RAM chip can be removed and a reversed engineered version of the chip that allows interface with a PC can be attached in it's place. After connecting the modified RAM chip to a PC, we can scan system memory until we find the key.
Once you have they key, you'll be able to run any code you want on the system. The storage NAND is a separate chip on the PCB, so replacing the RAM shouldn't effect it. This seems like a possible method to hack the system.
Anyone thought about trying?





