Tutorial Homebrew
Updated
Building Atmosphère on Windows using MSYS2
Sometimes you need to build the binaries for Atmosphère, or you want to change something on the source code, for building your starting point should be: https://github.com/Atmosphere-NX/Atmosphere/blob/master/docs/building.md
On that document you can read:
That instructions are a little plain for we the noobs.
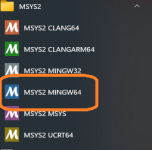
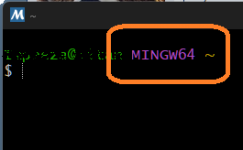
First you need Install a MSYS environment:
The latest instructions for install the MSYS environment are on https://gbatemp.net/threads/install-msys-environment.652234/ if you don't have one working, use them.
After you have the MSYS environment working you need to install DevKitPro
For that you can follow the instructions on the tutorial https://gbatemp.net/threads/setup-a-devkitpro-environment-on-windows.652238/
Now you can install DevKitPro packages:
And Atmosphère prerequisites
For me I had to add
Additional you need the packages
The package hactool need you to copy your own
LibNX Dependency
Atmosphère depends heavily on LibNX, generally when a major version of firmware is released or great changes on the code are made, changes to LibNX are also made.
The Atmosphère team works on their own repo of LibNX (https://github.com/Atmosphere-NX/libnx) and forward Pull Request to official SwitchBrew LibNX repo (https://github.com/switchbrew/libnx).
So if there are changes on LibNX you need to build it and install on your setup.
Now is time to build the binaries
Clone the repository:
Go to new created Atmosphère folder
Be sure you have defined the environment variables for DevKitPro
You can test it running the command
Copy prod.keys file on $HOME/.switch
And now you are ready to start the building process:
I do use the "-j$(nproc)" parameter to "bleed" all the available CPU to run the compiler, without that the whole process could take up to 1 hour.
I want to thank a lot to @binkinator and @godreborn for all the help and inspiration to make this guide, and want to ask you for help improving this guide.
Also special thanks to @godreborn for been a support of the users replies and suggestions to the OP.
Remember, as you are getting a new set of binaries, you need new set of sigpatches if you use it. So the great tool from @mrdude comes in hand, the latest release can be downloaded from: https://github.com/mrdude2478/IPS_Patch_Creator/releases/; you use the program to generate a new set of patches for your recently build package3 file.
Latest IPS Patch Creator:

-Edited: add sigpatches step and clean up a little-
-Edit 2, add LibNX build-
On that document you can read:
Building Atmosphère is a very straightforward process that relies almost exclusively on tools provided by the devkitPro organization.
Dependencies:
- devkitA64
- devkitARM
- Python 2 (Python 3 may work as well, but this is not guaranteed)
- LZ4
- PyCryptodome (optional)
- Hactool
Setup a DevKitPro environment: (https://devkitpro.org/wiki/Getting_Started)
Install the following packages via (dkp-)pacman:
- switch-dev
- switch-glm
- switch-libjpeg-turbo
- devkitARM
- devkitarm-rules
- hactool
Install the following library via python's package manager pip, required by exosphere:
- lz4
Finally, clone the Atmosphère repository and run make under its root directory.
That instructions are a little plain for we the noobs.
First you need Install a MSYS environment:
The latest instructions for install the MSYS environment are on https://gbatemp.net/threads/install-msys-environment.652234/ if you don't have one working, use them.
After you have the MSYS environment working you need to install DevKitPro
For that you can follow the instructions on the tutorial https://gbatemp.net/threads/setup-a-devkitpro-environment-on-windows.652238/
Now you can install DevKitPro packages:
Bash:
pacman -S --noconfirm switch-dev devkitA64 dkp-toolchain-vars libnx switch-tools switch-mesa switch-libdrm_nouveau switch-sdl2And Atmosphère prerequisites
Bash:
Pacman -Sy --noconfirm devkitA64 devkitARM devkitarm-rules hactool mingw-w64-x86_64-python mingw-w64-x86_64-python-lz4 mingw-w64-x86_64-python-pycryptodome switch-dev switch-glm switch-libjpeg-turbo mingw-w64-x86_64-python-pipFor me I had to add
zip package because even if wasn't explicit indicated on the build page, the code needs it.Additional you need the packages
git make lz4 for all to work, use the command:
Bash:
Pacman -Sy --noconfirm zip git make lz4The package hactool need you to copy your own
prod.keys file on $HOME/.switch folder. (c:\msys64\home\USERNAME\.switch if you use the default installation folder)LibNX Dependency
Atmosphère depends heavily on LibNX, generally when a major version of firmware is released or great changes on the code are made, changes to LibNX are also made.
The Atmosphère team works on their own repo of LibNX (https://github.com/Atmosphere-NX/libnx) and forward Pull Request to official SwitchBrew LibNX repo (https://github.com/switchbrew/libnx).
So if there are changes on LibNX you need to build it and install on your setup.
If you haven't done already, setup the environment variables
Test it running the command
Then go to the Atmosphere-NX/LibNX repo and look what is the new branch for the current firmware, by example, for Firmware 16.0.0 the branch name is "1600_Support"
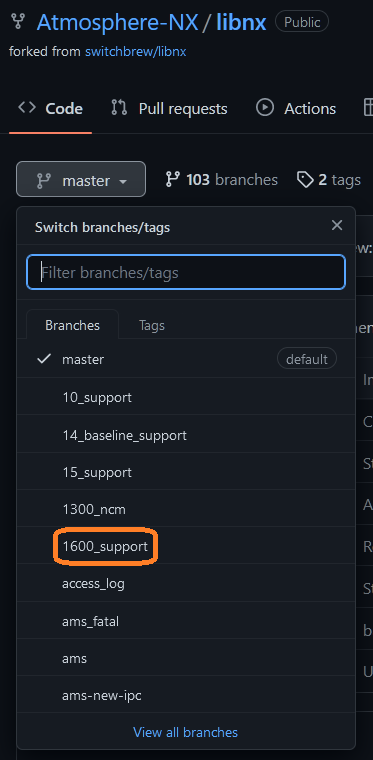
Then go to your MSYS MinGW64 window and clone the Atmosphere-NX/LibNX repo
And checkout the needed branch:
Then build and install the new LibNX libraries
Now you can build Atmosphère with latest LibNX code; remember if you update the pacman LibNX package the changes get reversed and you need to build LibNX again.
Bash:
export DEVKITPRO=/opt/devkitpro
export DEVKITARM=${DEVKITPRO}/devkitARM
export DEVKITPPC=${DEVKITPRO}/devkitPPC
export PATH=${DEVKITPRO}/tools/bin:$PATHTest it running the command
exportThen go to the Atmosphere-NX/LibNX repo and look what is the new branch for the current firmware, by example, for Firmware 16.0.0 the branch name is "1600_Support"
Then go to your MSYS MinGW64 window and clone the Atmosphere-NX/LibNX repo
Bash:
cd ~
git clone --recursive https://github.com/Atmosphere-NX/libnx.git
cd libnxAnd checkout the needed branch:
Bash:
git checkout 1600_supportThen build and install the new LibNX libraries
Bash:
make install -j$(nproc)Now you can build Atmosphère with latest LibNX code; remember if you update the pacman LibNX package the changes get reversed and you need to build LibNX again.
Now is time to build the binaries
Clone the repository:
Bash:
cd ~
git clone --recursive https://github.com/Atmosphere-NX/AtmosphereGo to new created Atmosphère folder
Bash:
cd AtmosphereBe sure you have defined the environment variables for DevKitPro
Bash:
export DEVKITPRO=/opt/devkitpro
export DEVKITARM=${DEVKITPRO}/devkitARM
export DEVKITPPC=${DEVKITPRO}/devkitPPC
export PATH=${DEVKITPRO}/tools/bin:$PATHYou can test it running the command
exportCopy prod.keys file on $HOME/.switch
Bash:
mkdir ~/.switch
cp YOURCURRENTPATHTOKEYS ~/.switch/prod.keysAnd now you are ready to start the building process:
Bash:
make -j$(nproc)I do use the "-j$(nproc)" parameter to "bleed" all the available CPU to run the compiler, without that the whole process could take up to 1 hour.
I want to thank a lot to @binkinator and @godreborn for all the help and inspiration to make this guide, and want to ask you for help improving this guide.
Also special thanks to @godreborn for been a support of the users replies and suggestions to the OP.
Remember, as you are getting a new set of binaries, you need new set of sigpatches if you use it. So the great tool from @mrdude comes in hand, the latest release can be downloaded from: https://github.com/mrdude2478/IPS_Patch_Creator/releases/; you use the program to generate a new set of patches for your recently build package3 file.
Latest IPS Patch Creator:
-Edited: add sigpatches step and clean up a little-
-Edit 2, add LibNX build-
Attachments
Last edited by impeeza,