- Joined
- Apr 18, 2013
- Messages
- 1,768
- Trophies
- 2
- Location
- on the cool side of the pillow
- Website
- follow-the-white-rabbit.wtf
- XP
- 3,017
- Country

Hello,
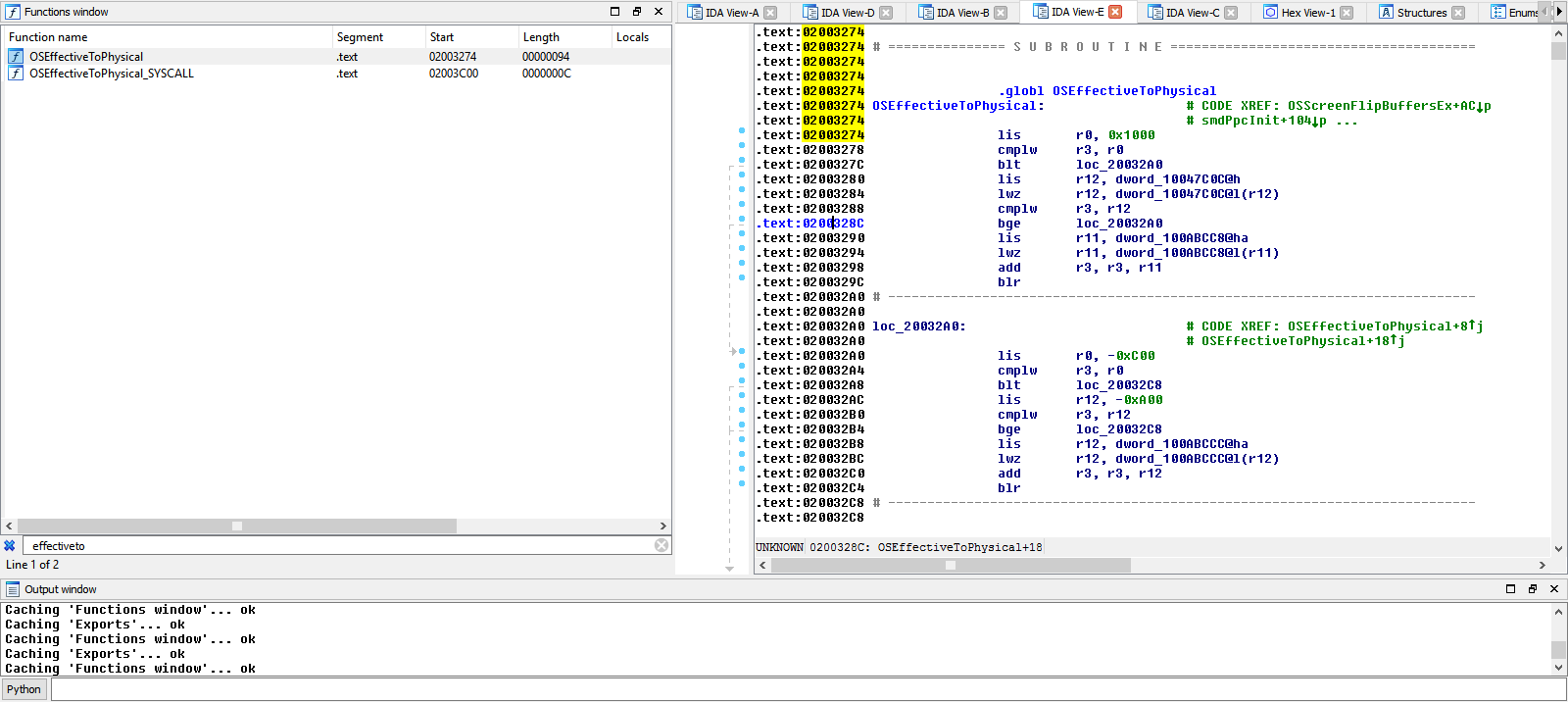
in order to allow the codehandler to write values to the executable memory range I need to convert the cheat's address from effective to physical and then perform a memory copy syscall to get the value written to the executable memory.
However, everytime I attempt to do a syscall the console freezes.
Here's some information:
Cheat code layout for 32-bit writes:
00020000 LLLLLLLL
VVVVVVVV 00000000
LLLLLLLL = Address
VVVVVVVV = Value
syscall to convert the address inside of r3 from effective to physical:
li r0, 0x0200
sc
syscall to perform a mem_copy write:
li r0, 0x2500
sc
r3 contains the physical address to copy to
r4 contains the address to copy from
r5 contains the buffer size (0x04 for 32-bits)
the codehandler always holds the address of the current cheat's first byte in r6
For troubleshooting I want first to perform the effective-to-physical syscall:
This does not work (even I can perform a few other sc this way like fast_exit)
So I thought the system does not know where to branch because the sc ends with blr and the lr (link register) was not set.
blr returns to the address inside of lr + 0x04. In this case to the nop instruction
So I tried to backup lr to r20, load the sc's address into r21, load r21 into lr and after blr reloading r20 back into lr.
Sadly this does not work as well
Now I had a look at a .elf to see how syscalls are performed there. I recreated my syscall based on this scheme. But it froze again..:
Any idea what to do?
@wj44 @NWPlayer123 @BullyWiiPlaza @Maschell
in order to allow the codehandler to write values to the executable memory range I need to convert the cheat's address from effective to physical and then perform a memory copy syscall to get the value written to the executable memory.
However, everytime I attempt to do a syscall the console freezes.
Here's some information:
Cheat code layout for 32-bit writes:
00020000 LLLLLLLL
VVVVVVVV 00000000
LLLLLLLL = Address
VVVVVVVV = Value
syscall to convert the address inside of r3 from effective to physical:
li r0, 0x0200
sc
syscall to perform a mem_copy write:
li r0, 0x2500
sc
r3 contains the physical address to copy to
r4 contains the address to copy from
r5 contains the buffer size (0x04 for 32-bits)
the codehandler always holds the address of the current cheat's first byte in r6
For troubleshooting I want first to perform the effective-to-physical syscall:
Code:
lis r4, 0x1001 // address where to copy the data to
ori r4, r4, 0x5000 // "
lwz r5, 0x08 (r6) // load cheat value
stw r5, 0x00 (r4) // copy cheat value to 0x10015000
lwz r3, 0x04 (r6) // load cheat address
li r0, 0x0200 // load effective to physical sc value
sc // perform effective to physical. System crashes here
nop // nop here because returning from sc can skip an instruction
addi r6, r6, 0x10 // prepare r6 to read the next cheat
b 0x0000019C // go back to the codetype-checkThis does not work (even I can perform a few other sc this way like fast_exit)
So I thought the system does not know where to branch because the sc ends with blr and the lr (link register) was not set.
blr returns to the address inside of lr + 0x04. In this case to the nop instruction
So I tried to backup lr to r20, load the sc's address into r21, load r21 into lr and after blr reloading r20 back into lr.
Sadly this does not work as well
Code:
mflr r20 // backup lr into r20
lis r4, 0x1001 // address where to copy the data to
ori r4, r4, 0x5000 // "
lwz r5, 0x08 (r6) // load cheat value
stw r5, 0x00 (r4) // copy cheat value to 0x10015000
lwz r3, 0x04 (r6) // load cheat address
li r0, 0x0200 // load effective to physical sc value
lis r21, 0x010F // load sc's address into r21
ori r21, 0x4000 // "
mtlr r21 // move r21 to lr
sc // effective to physical. System crashes here
nop // nop here because returning from sc can skip an instruction
mtlr r20 // put r20 back into lr so the codehandler will return properly
addi r6, r6, 0x10
b 0x0000019CNow I had a look at a .elf to see how syscalls are performed there. I recreated my syscall based on this scheme. But it froze again..:
Code:
mflr r0 // backup lr into r0
mr r20, r0 // move r0 into r20
lis r3, 0x1001 // load address to be converted into r3
ori r3, r3, 0x5000 // "
li r0, 0x0200 // load sc value
sc // perform syscall
nop
mr r0, r20 // put r20 back into r0
mtlr // put r0 back to lrAny idea what to do?
@wj44 @NWPlayer123 @BullyWiiPlaza @Maschell
Last edited by CosmoCortney,