For executing assembly in the form of a char array I wrote the following code:
The client sends the length of the assembly bytes and the assembly bytes themselves:
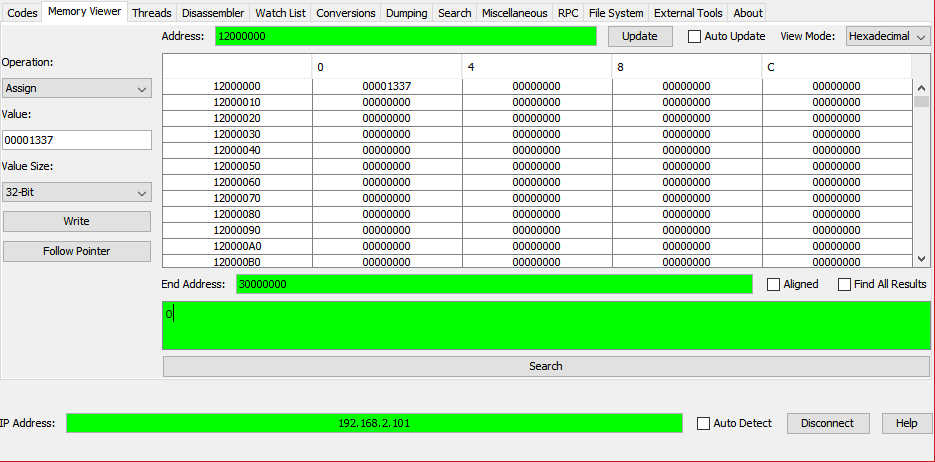
When I use this e.g. like with the following assembly:
The console crashes with an Exception ISI:

The code dump shows the assembly I gave it to execute and how a blr instruction is added at the end so the code returns to the caller. Furthermore, the link register LR contains an invalid address which might have been the reason for the crash.
Why is this happening and how to fix it? I guess the intention is clear: I want to send over some bytes and have them execute via the TCP Gecko Installer thread and continue its execution right after.
@NWPlayer123
@QuarkTheAwesome
@FIX94
@dimok
@Maschell
@CosmoCortney
Code:
#define ASSEMBLY_BUFFER_SIZE 0x190
Code:
void receiveString(struct pygecko_bss_t *bss,
int clientfd,
char *stringBuffer,
int bufferSize) {
// Receive the string length
char lengthBuffer[4] = {0};
int ret = recvwait(bss, clientfd, lengthBuffer, 4);
ASSERT_FUNCTION_SUCCEEDED(ret, "recvwait (string length)")
int stringLength = ((int *) lengthBuffer)[0];
if (stringLength >= 0 && stringLength <= bufferSize) {
// Receive the actual string
ret = recvwait(bss, clientfd, stringBuffer, stringLength);
ASSERT_FUNCTION_SUCCEEDED(ret, "recvwait (string)")
} else {
OSFatal("String buffer size exceeded");
}
}
Code:
case COMMAND_EXECUTE_ASSEMBLY: {
char assemblyBuffer[ASSEMBLY_BUFFER_SIZE] = {0};
// Receive the assembly
receiveString(bss, clientfd, assemblyBuffer, ASSEMBLY_BUFFER_SIZE);
// Execute the assembly
void (*function)() = (void *) assemblyBuffer;
function();
break;
}
Code:
public void executeAssembly(byte[] assembly) throws Exception
{
int assemblyLength = assembly.length;
if (assemblyLength <= 0 || assemblyLength % 4 != 0)
{
throw new IllegalStateException("Bad assembly bytes length: " + assemblyLength);
}
assembly = Assembler.forceReturnStatement(assembly);
try (CloseableReentrantLock ignored = reentrantLock.acquire())
{
sendCommand(Command.EXECUTE_ASSEMBLY);
dataSender.writeInt(assembly.length);
dataSender.write(assembly);
dataSender.flush();
}
}
Code:
byte[] bytes = Assembler.assembleBytes("lis r12, 0x1200\n" +
"ori r12, r12, 0x0000\n" +
"li r11, 0x1337\n" +
"stw r11, 0 (r12)");
executeAssembly(bytes);
The code dump shows the assembly I gave it to execute and how a blr instruction is added at the end so the code returns to the caller. Furthermore, the link register LR contains an invalid address which might have been the reason for the crash.
Why is this happening and how to fix it? I guess the intention is clear: I want to send over some bytes and have them execute via the TCP Gecko Installer thread and continue its execution right after.
@NWPlayer123
@QuarkTheAwesome
@FIX94
@dimok
@Maschell
@CosmoCortney