Vanilla atmosphere doesn't support pirated nspsIf I switch over from Reinx to atmosphere will my games and stuff be still there?
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I wonder if they've properly pwned TSEC or if it's just dumping the keys.
Will be interesting to see Nintendo's stability response to this either way.
Will be interesting to see Nintendo's stability response to this either way.
A lot of people, plus TX ready to ''borrow'' the codesNice, I'm sure a lot of people were waiting for this.
type F to pay respect.
joke aside, it's nice that new CFWW won't create crash report, that means more stealth!
Last edited by leon315,
Vanilla atmosphere doesn't support pirated nsps
These patches may or may not work with 6.2 https://gbatemp.net/threads/i-heard-that-you-guys-need-some-sweet-patches-for-atmosphere.521164/
I wonder if they've properly pwned TSEC or if it's just dumping the keys.
It looks like the exploit that mathileu described.
https://github.com/Atmosphere-NX/Atmosphere/commit/ed3770691519f025b5e7ebe353afa0fd3b224fd6
I'm not convinced it's possible to actually hack TSEC any other way, so it will be interesting how Nintendo will block it and whether 6.2 is going to turn out to be the highest we will ever be able to run.
Last edited by smf,
Damn was hoping to try out smashVanilla atmosphere doesn't support pirated nsps
oh well guess i'll just wait
is there a way to remove some update folder to never update the switch, just as there was a way on Wii U?
D
Deleted-471350
Guest
I wonder if they've properly pwned TSEC or if it's just dumping the keys.
Will be interesting to see Nintendo's stability response to this either way.
I can answer this, since I fully understand how this sploit works (and wrote it independently myself).
They did not pwn TSEC at all. What the sploit does is fool TSEC into thinking it's running with sole full control of the system (it thinks the CPUs / DMA are halted). Only then will it continue to generate the keys and decrypt the package1. To fool the TSEC, it needs to read the same constant values from MMIO memory space. This can be done by remapping the address space into DRAM by using SMMU translation. If a single bit from this space is different (like say the BPMP CPU is still running, the IO space would reflect that) then the TSEC would detect it. But by mimicing the same values in DRAM, the TSEC is fooled and continues decrypting package1.
To actually pwn TSEC you need to get code execution in the authenticated mode of the TSEC, which can then be used to reveal TSEC secrets. To date, nobody (and I'm pretty sure not even reswitched or switchbrew) has managed to do this.
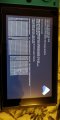
That's a very pretty picture, good resolution, the text looks great. Perhaps it's that the error reporting code uses good anti-aliasing, or perhaps it is the camera, no idea.Error. I have placed all files in root SD and booted fusee primary bin payload. Goes through the black atmosphere welcome and set up, then nintendo logo, then switch logo, then this.
Please help
Isnt every NSP pirated by definition?Vanilla atmosphere doesn't support pirated nsps
And then the next day, "SXOS rocking the Switch scene 2018!"
"and beyond"...And then the next day, "SXOS rocking the Switch scene 2018!"
*So long as we have community projects to steal code from"and beyond*"...
You need to "*"
Well I hope they release version 3.0 including gui changes along with 6.2 compatibility. Maybe they'll even throw in NSP install to hdd. fingers crossed.
Can nintendo with an update change how this is handled so the TSEC wont give the keys?I can answer this, since I fully understand how this sploit works (and wrote it independently myself).
They did not pwn TSEC at all. What the sploit does is fool TSEC into thinking it's running with sole full control of the system (it thinks the CPUs / DMA are halted). Only then will it continue to generate the keys and decrypt the package1. To fool the TSEC, it needs to read the same constant values from MMIO memory space. This can be done by remapping the address space into DRAM by using SMMU translation. If a single bit from this space is different (like say the BPMP CPU is still running, the IO space would reflect that) then the TSEC would detect it. But by mimicing the same values in DRAM, the TSEC is fooled and continues decrypting package1.
To actually pwn TSEC you need to get code execution in the authenticated mode of the TSEC, which can then be used to reveal TSEC secrets. To date, nobody (and I'm pretty sure not even reswitched or switchbrew) has managed to do this.
D
Deleted-471350
Guest
Can nintendo with an update change how this is handled so the TSEC wont give the keys?
Yes they can. Mimicing MMIO with exactly the same behavior from a CPU is not trivial. What the TSEC now checks is mostly static data. If they change the TSEC to start to check for dynamic behavior of MMIO memory, well let's say it may not be possible to bypass it. There are also probably more than just one way to detect this hack.
Last edited by ,
You can just add the sigpatches bundled with Kosmos. I use these with vanilla Atmosphere.Vanilla atmosphere doesn't support pirated nsps
Something being a certain filetype does not make it pirated. Also dumping your own games as NSP would not be piracy.Isnt every NSP pirated by definition?
Similar threads
-
- Portal
- Replies
- 94
- Views
- 20K
-
- Portal
- Replies
- 88
- Views
- 32K
- Replies
- 0
- Views
- 1K
-
- Portal
- Replies
- 51
- Views
- 24K
- Replies
- 0
- Views
- 12K
Site & Scene News
New Hot Discussed
-
-
57K views
Nintendo Switch firmware 18.0.0 has been released
It's the first Nintendo Switch firmware update of 2024. Made available as of today is system software version 18.0.0, marking a new milestone. According to the patch... -
28K views
GitLab has taken down the Suyu Nintendo Switch emulator
Emulator takedowns continue. Not long after its first release, Suyu emulator has been removed from GitLab via a DMCA takedown. Suyu was a Nintendo Switch emulator... -
20K views
Atmosphere CFW for Switch updated to pre-release version 1.7.0, adds support for firmware 18.0.0
After a couple days of Nintendo releasing their 18.0.0 firmware update, @SciresM releases a brand new update to his Atmosphere NX custom firmware for the Nintendo...by ShadowOne333 94 -
17K views
Wii U and 3DS online services shutting down today, but Pretendo is here to save the day
Today, April 8th, 2024, at 4PM PT, marks the day in which Nintendo permanently ends support for both the 3DS and the Wii U online services, which include co-op play...by ShadowOne333 176 -
16K views
Denuvo unveils new technology "TraceMark" aimed to watermark and easily trace leaked games
Denuvo by Irdeto has unveiled at GDC (Game Developers Conference) this past March 18th their brand new anti-piracy technology named "TraceMark", specifically tailored...by ShadowOne333 101 -
15K views
GBAtemp Exclusive Introducing tempBOT AI - your new virtual GBAtemp companion and aide (April Fools)
Hello, GBAtemp members! After a prolonged absence, I am delighted to announce my return and upgraded form to you today... Introducing tempBOT AI 🤖 As the embodiment... -
11K views
Pokemon fangame hosting website "Relic Castle" taken down by The Pokemon Company
Yet another casualty goes down in the never-ending battle of copyright enforcement, and this time, it hit a big website which was the host for many fangames based and...by ShadowOne333 65 -
11K views
MisterFPGA has been updated to include an official release for its Nintendo 64 core
The highly popular and accurate FPGA hardware, MisterFGPA, has received today a brand new update with a long-awaited feature, or rather, a new core for hardcore...by ShadowOne333 51 -
10K views
Apple is being sued for antitrust violations by the Department of Justice of the US
The 2nd biggest technology company in the world, Apple, is being sued by none other than the Department of Justice of the United States, filed for antitrust...by ShadowOne333 80 -
10K views
Homebrew SpotPass Archival Project announced
With Nintendo ceasing online communication for Nintendo 3DS, 2DS and Wii U systems next month, SpotPass data distribution will be halted. This will in turn affect...
-
-
-
223 replies
Nintendo Switch firmware 18.0.0 has been released
It's the first Nintendo Switch firmware update of 2024. Made available as of today is system software version 18.0.0, marking a new milestone. According to the patch...by Chary -
176 replies
Wii U and 3DS online services shutting down today, but Pretendo is here to save the day
Today, April 8th, 2024, at 4PM PT, marks the day in which Nintendo permanently ends support for both the 3DS and the Wii U online services, which include co-op play...by ShadowOne333 -
169 replies
GBAtemp Exclusive Introducing tempBOT AI - your new virtual GBAtemp companion and aide (April Fools)
Hello, GBAtemp members! After a prolonged absence, I am delighted to announce my return and upgraded form to you today... Introducing tempBOT AI 🤖 As the embodiment...by tempBOT -
146 replies
GitLab has taken down the Suyu Nintendo Switch emulator
Emulator takedowns continue. Not long after its first release, Suyu emulator has been removed from GitLab via a DMCA takedown. Suyu was a Nintendo Switch emulator...by Chary -
101 replies
Denuvo unveils new technology "TraceMark" aimed to watermark and easily trace leaked games
Denuvo by Irdeto has unveiled at GDC (Game Developers Conference) this past March 18th their brand new anti-piracy technology named "TraceMark", specifically tailored...by ShadowOne333 -
95 replies
The first retro emulator hits Apple's App Store, but you should probably avoid it
With Apple having recently updated their guidelines for the App Store, iOS users have been left to speculate on specific wording and whether retro emulators as we...by Scarlet -
94 replies
Atmosphere CFW for Switch updated to pre-release version 1.7.0, adds support for firmware 18.0.0
After a couple days of Nintendo releasing their 18.0.0 firmware update, @SciresM releases a brand new update to his Atmosphere NX custom firmware for the Nintendo...by ShadowOne333 -
80 replies
Apple is being sued for antitrust violations by the Department of Justice of the US
The 2nd biggest technology company in the world, Apple, is being sued by none other than the Department of Justice of the United States, filed for antitrust...by ShadowOne333 -
65 replies
Pokemon fangame hosting website "Relic Castle" taken down by The Pokemon Company
Yet another casualty goes down in the never-ending battle of copyright enforcement, and this time, it hit a big website which was the host for many fangames based and...by ShadowOne333 -
51 replies
MisterFPGA has been updated to include an official release for its Nintendo 64 core
The highly popular and accurate FPGA hardware, MisterFGPA, has received today a brand new update with a long-awaited feature, or rather, a new core for hardcore...by ShadowOne333
-
Popular threads in this forum
General chit-chat
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
 @
Xdqwerty:
something about ea reverse engineering the genesis so they could make their games there+1
@
Xdqwerty:
something about ea reverse engineering the genesis so they could make their games there+1 -
-
 @
BakerMan:
if they get permission from 4j (the studio who helped put minecraft on consoles), they could put the console edition tutorial worlds in the game, as seeds+1
@
BakerMan:
if they get permission from 4j (the studio who helped put minecraft on consoles), they could put the console edition tutorial worlds in the game, as seeds+1
and i mean all of them (if not, maybe a few highlights, like TU1, TU31, and TU69) -
-
-
-
-
-
-
-