You must've not looked at that thread where I said he was wrong, he's not updated the thing for whatever reason. I don't knwo why, since he's spreading false information that makes people think the thing's harder than it actually is. His numbers _only_ apply symmetric encryption. Aka AES, and other such ones where you have 1 key. rsa is way way easier. Right now people are advised to use 4096bit rsa whilst only using 128bit aes on their sites is more than enough. So you can clearly see the big divide there.I dont hawe onebut will decapping help that somehow?
Cool, those are great newsI remember when Rydian said it would take million years to crack the key.. but hearing this now sounds so cool

You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
I don't know what encryption the 3DS uses.
My point was that I highly doubt that its 128bit RSA (because it would be extremely easy to crack)
I did not say that I can crack the 3DS.
My point was that I highly doubt that its 128bit RSA (because it would be extremely easy to crack)
I did not say that I can crack the 3DS.
According to DSi Brew the DS uses a 1024 bit RSA key. With how much more advanced the 3ds is, there's no way it uses a less secure key.
http://dsibrew.org/wiki/NDS_Format
http://dsibrew.org/wiki/NDS_Format
from what I gather from http://www.3dbrew.org/wiki/Title_metadata#Signature_Type
the 3DS carts can use 4096bit RSA, 2048bit RSA and 480bit ECDSA
Additionally I don't think that 1024bit RSA can be cracked outside spook circles.
But I'd be interested in any sources you can provide.
the 3DS carts can use 4096bit RSA, 2048bit RSA and 480bit ECDSA
Additionally I don't think that 1024bit RSA can be cracked outside spook circles.
But I'd be interested in any sources you can provide.
Ah OK, it says that the guy did 768bit rsa and cracked multiple keys using 75$ and rsa. Seems I remembered the story wrong/too happily, well there goes that then. Here's hoping nintendo's rng they used was as dumb as sony's with ecdsa.
He was not wrong. He was talking about bruteforcing the common key. You are talking about factoring the private key, which necessitates having the common (i.e. public) key first. From discussions on IRC, I don't believe even yellows8 or neimod have that, despite all their impressive software and hardware based hacks. I recall yellows8 mentioning the use of what he called an "oracle" unit for decryption, which essentially meant an exploited 3DS unit. (I think at the time the way it was done was to provide the 3DS with whatever data they had that was encrypted, wait for it to decrypt it and pull the decrypted content out of RAM, but this was a while ago and I may be remembering some details incorrectly).You must've not looked at that thread where I said he was wrong, he's not updated the thing for whatever reason. I don't knwo why, since he's spreading false information that makes people think the thing's harder than it actually is. His numbers _only_ apply symmetric encryption. Aka AES, and other such ones where you have 1 key. rsa is way way easier. Right now people are advised to use 4096bit rsa whilst only using 128bit aes on their sites is more than enough. So you can clearly see the big divide there.
EDIT: Judging by your post above, your earlier claims that 2048-bit RSA could be cracked for $100 of EC2 are obviously wrong. Can't say I'm surprised.
I've heard of those kinds of oracle's before, and with the chip being desoldered it's not going to take that long anyway. RSA keys have to have to be related. So it's not 2^128 that's impossible, as each and every 128bit number(if we're talking about 128bit rsa) cannot be prime. Prime numbers get smaller and smaller as you go up. So his numbers are still wrong. Even brute forcing the public key wouldn't take millions of years. There aren't that many public private key pairs out there. I mean yes there are tons but not 2^128 as he was talking about. The amount of primes that relate to eachother as defined in RSA is miniscule when compared to the total keyspace of a 128bit key.He was not wrong. He was talking about bruteforcing the common key. You are talking about factoring the private key, which necessitates having the common (i.e. public) key first. From discussions on IRC, I don't believe even yellows8 or neimod have that, despite all their impressive software and hardware based hacks. I recall yellows8 mentioning the use of what he called an "oracle" unit for decryption, which essentially meant an exploited 3DS unit. (I think at the time the way it was done was to provide the 3DS with whatever data they had that was encrypted, wait for it to decrypt it and pull the decrypted content out of RAM, but this was a while ago and I may be remembering some details incorrectly).
For 2048 or 4096 bit RSA Neimod would need access to that fabled NSA (or insert another intelligence agency here) key breaking super computer rumored about in dubious conspiracy theory circles pretty much since the widespread use of encryption (and after the NSA backdoor plot failed/backdoor rumours died down).
I've heard of those kinds of oracle's before, and with the chip being desoldered it's not going to take that long anyway. RSA keys have to have to be related. So it's not 2^128 that's impossible, as each and every 128bit number(if we're talking about 128bit rsa) cannot be prime. Prime numbers get smaller and smaller as you go up. So his numbers are still wrong. Even brute forcing the public key wouldn't take millions of years. There aren't that many public private key pairs out there. I mean yes there are tons but not 2^128 as he was talking about. The amount of primes that relate to eachother as defined in RSA is miniscule when compared to the total keyspace of a 128bit key.
I have to be honest, I don't completely understand the RSA algorithm. Do both keys have to be prime numbers? Is there some easy way to check if a number is prime or not? Because surely you'll still have to go through every number and check if it's prime before rejecting it and moving onto the next? From what I know of primes, while the gaps between primes can be very roughly estimated, they cannot be accurately estimated, and there are plenty of "anomalies" where primes appear much closer together than expected etc. Which would mean the only way to be sure if a number is prime or not is to check, and depending on how long that takes, it may well be quicker just to test decryption with that key rather than check if the key is prime.
Anyhow, the 3DS uses more than one key pair; http://www.3dbrew.org/wiki/AES#Keyslots
[Apologies if anything I'm saying here isn't correct]
You could simply have folders with every 3DS rom on one microSD and use an old DS flashcard to go in and cut the main rom in the root folder back to its game folder and move another game into the root folder.
I'm ashuming you will like need to name it a certain name like 'main' ect.
so every folder has the name of the game and the 'main.3ds(?)' in it, then it would be easy to swap games.
I'm ashuming you will like need to name it a certain name like 'main' ect.
so every folder has the name of the game and the 'main.3ds(?)' in it, then it would be easy to swap games.
Repeating this isn't going to make it more likely to happen.
Seeing an error will do what, exactly? Nothing. If you really want to see it, just stick an old DS flashcard or un-updated DSi flashcard into a 3DS. Same error will show as would with an unsigned ROM on this card.
EDIT: This is the error:
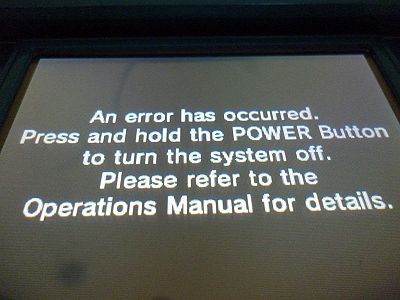
im sure people will experiment with this.. maybe some CIA files CCI CXI
Both numbers have to be prime, both numbers have to be the length specified(128bits in this example) they must also both be related, and they both _should_ be random. There are quite a few algorithms for testing whether a number is prime or not, that don't require you to literally try every single number that is less than 1 of the number you're checking. If you can find the public key, which has to be known on the 3ds it has to be stored there or else it'd not be able to verify anything. if it's in hardware the decapping would probably reveal where it is hidden and help people know where to look for the thing. I seriously doubt nintendo paid for hardware that checks against tampering and then kills itself if someone tries to find the thing, and does all of the crypto in the black box, as this is a console and is meant to be very very cost effective and those boxes are unbelieveably expensive and are only really seen/used by CAs(people who make SSL certs).I have to be honest, I don't completely understand the RSA algorithm. Do both keys have to be prime numbers? Is there some easy way to check if a number is prime or not? Because surely you'll still have to go through every number and check if it's prime before rejecting it and moving onto the next? From what I know of primes, while the gaps between primes can be very roughly estimated, they cannot be accurately estimated, and there are plenty of "anomalies" where primes appear much closer together than expected etc. Which would mean the only way to be sure if a number is prime or not is to check, and depending on how long that takes, it may well be quicker just to test decryption with that key rather than check if the key is prime.
Anyhow, the 3DS uses more than one key pair; http://www.3dbrew.org/wiki/AES#Keyslots
Now then it could and likely is using lots of different keys, still though the public key is exposed with each signature so you can verify it, if nintendo made it so that the key's in hardware IE it cannot be updated, then they wouldn't have to include it in the signature, but it's much more likely it's stored on some eeprom that can be overwritten with a new key if peopel figure it out(like the ps3). So if we decap it, someone gets literal hardware access to the thing, sees how everything works/looks it's end of it all. If they're including the public key with each signature(not much security loss with doing this) then you'd just have to find the thing and bam you're done. They're also likely if they've got the ability to add new keys going to be transmitting it in the firmware. Now then I seriously doubt they're going to be a sony thing again, sony did their own thing and failed hard. Nintendo has RSA doing it, the company that literally made this thing. So they're likely using everythign as it should be. I'd even guess that they have a hardware chip to do the AES, Sha1/256/512, and the RSA verifications.
Edit: and to just reiterate the keys have to be there, even if they're hiding them. Using oracle attacks against them, you'll eventually learn what the key is. We already have dumps of roms, so you have the signature there. You know what you're trying for. Now you just need the public key to verify. It has to be on the system, it has to be in there. And also like the ps3, they can't just revoke the old key, once it's factored that's it. They can force _new_ games to use the new key, but people will resign the old games to make them work with the older software. This is assuming they've went full out on this thing.
Edit 2: Btw that's AES, you don't need AES to run signed code. That's symmetric encryption, that's to _decrypt_ games and such. But to make your homebrew looke legit, you will be using the RSA keypair. So whilst that's interesting that they've chosen so many different ways to encrypting/decrypting, the key still has to be stored in the games to decrypt them. If they're stored encrypted, then the 3ds might have its own private key to decrypt the roms, and nintendo encrypts them with a public key for each region. Doing this would cause more headaches/work as you'd need to factor more stuff. But still if you've got the hardware schematics before you, you'll find a flaw in the system.
This stuff wasn't written by perfect gods, it was written by men. Even RSA can get hacked, evne they can screw up, no one's perfect. There are flaws, there is holes in there, it's just with each generation they get harder and harder to find.
ThanksI'd imagine a week or so before retailers get it. But I just asked them if they knew when they were sending it out. Waiting for a reply now. I'm sure they want to get the kinks out before sending it off to be reviewed.
"RAM Tracing" was the phrase used, and they had a trace from boot that measured like 50+ GB or something like that to initially run through if I'm remebering the right number.(I think at the time the way it was done was to provide the 3DS with whatever data they had that was encrypted, wait for it to decrypt it and pull the decrypted content out of RAM, but this was a while ago and I may be remembering some details incorrectly).
I was looking up how exactly 3DS roms were being dumped and happened upon an old thread here on the temp that wound up in EOF (because I guess it was pointless at the time...)
Lol...it's funny how this applies, why wasn't the idea behind this cart used sooner? Was the 'trick' really that complicated? It doesn't seem like it. Didn't they just solder on an sd slot to where the rom used to be stored?What if the secret to playing ROM backups was something super obvious that everyone overlooked?
http://www.3dbrew.org/wiki/NCSD "...is the format of retail game ROM dumps." "RSA-2048 SHA-256 signature of the NCSD header "Both numbers have to be prime, both numbers have to be the length specified(128bits in this example) they must also both be related, and they both _should_ be random. There are quite a few algorithms for testing whether a number is prime or not, that don't require you to literally try every single number that is less than 1 of the number you're checking. If you can find the public key, which has to be known on the 3ds it has to be stored there or else it'd not be able to verify anything. if it's in hardware the decapping would probably reveal where it is hidden and help people know where to look for the thing. I seriously doubt nintendo paid for hardware that checks against tampering and then kills itself if someone tries to find the thing, and does all of the crypto in the black box, as this is a console and is meant to be very very cost effective and those boxes are unbelieveably expensive and are only really seen/used by CAs(people who make SSL certs).
Now then it could and likely is using lots of different keys, still though the public key is exposed with each signature so you can verify it, if nintendo made it so that the key's in hardware IE it cannot be updated, then they wouldn't have to include it in the signature, but it's much more likely it's stored on some eeprom that can be overwritten with a new key if peopel figure it out(like the ps3). So if we decap it, someone gets literal hardware access to the thing, sees how everything works/looks it's end of it all. If they're including the public key with each signature(not much security loss with doing this) then you'd just have to find the thing and bam you're done. They're also likely if they've got the ability to add new keys going to be transmitting it in the firmware. Now then I seriously doubt they're going to be a sony thing again, sony did their own thing and failed hard. Nintendo has RSA doing it, the company that literally made this thing. So they're likely using everythign as it should be. I'd even guess that they have a hardware chip to do the AES, Sha1/256/512, and the RSA verifications.
Edit: and to just reiterate the keys have to be there, even if they're hiding them. Using oracle attacks against them, you'll eventually learn what the key is. We already have dumps of roms, so you have the signature there. You know what you're trying for. Now you just need the public key to verify. It has to be on the system, it has to be in there. And also like the ps3, they can't just revoke the old key, once it's factored that's it. They can force _new_ games to use the new key, but people will resign the old games to make them work with the older software. This is assuming they've went full out on this thing.
Edit 2: Btw that's AES, you don't need AES to run signed code. That's symmetric encryption, that's to _decrypt_ games and such. But to make your homebrew looke legit, you will be using the RSA keypair. So whilst that's interesting that they've chosen so many different ways to encrypting/decrypting, the key still has to be stored in the games to decrypt them. If they're stored encrypted, then the 3ds might have its own private key to decrypt the roms, and nintendo encrypts them with a public key for each region. Doing this would cause more headaches/work as you'd need to factor more stuff. But still if you've got the hardware schematics before you, you'll find a flaw in the system.
This stuff wasn't written by perfect gods, it was written by men. Even RSA can get hacked, evne they can screw up, no one's perfect. There are flaws, there is holes in there, it's just with each generation they get harder and harder to find.
RSA-2048 signature = two 1024 bit prime numbers. Good luck getting those two, when you do, call me. I need to know if using websites and other forms of online communication secured with 2048-bit RSA, aren't as secure as I thought they were.
Although I could be wrong, and everyone who uses RSA-2048 or greater could have been tricked into thinking it's secure. You have a chance to point out how stupid I am to be speaking about subjects I obviously don't understand. The RSA-2048 public keys used to verify Tickets and TMD, are publicly available (in the certificate chain of a TMD or ticket from Nintendo's CDN). And if you know what you're talking about you'll be able to get them in less than 5 minutes.
seeing the hands of the "lady" from the video, i'd say they're pretty much chinese
Wow. Firstly you can tell Chinese vs any other Asian nation simply from a hand? That's pretty impressive.
Secondly. You may not have noticed, but there are actually Chinese people, and people of Chinese descent (but maybe your hand-recognising algorithm can detect that?) living outside of China.
I wonder how they would go about doing that?- Can it play games from other regions?
Currently no, however due to popular demand, we have launched an investigation into this possibility.
I'm just really curious about how they would do that.
I read it as "as soon as somebody else finds a genuine hack, we'll incorporate it into the firmware of the card if at all possible. But that's just the sceptic in me...
Wow. Firstly you can tell Chinese vs any other Asian nation simply from a hand? That's pretty impressive.
Secondly. You may not have noticed, but there are actually Chinese people, and people of Chinese descent (but maybe your hand-recognising algorithm can detect that?) living outside of China.
I read it as "as soon as somebody else finds a genuine hack, we'll incorporate it into the firmware of the card if at all possible. But that's just the sceptic in me...
but they're still from China
You know, it's possible for people from one country to go to another and have a child there.but they're still from China
- Status
- Not open for further replies.
Similar threads
- Replies
- 14
- Views
- 662
- Replies
- 3
- Views
- 448
- Replies
- 31
- Views
- 9K
Site & Scene News
New Hot Discussed
-
-
25K views
Wii U and 3DS online services shutting down today, but Pretendo is here to save the day
Today, April 8th, 2024, at 4PM PT, marks the day in which Nintendo permanently ends support for both the 3DS and the Wii U online services, which include co-op play...by ShadowOne333 179 -
22K views
Nintendo Switch firmware update 18.0.1 has been released
A new Nintendo Switch firmware update is here. System software version 18.0.1 has been released. This update offers the typical stability features as all other... -
18K views
The first retro emulator hits Apple's App Store, but you should probably avoid it
With Apple having recently updated their guidelines for the App Store, iOS users have been left to speculate on specific wording and whether retro emulators as we... -
18K views
Delta emulator now available on the App Store for iOS
The time has finally come, and after many, many years (if not decades) of Apple users having to side load emulator apps into their iOS devices through unofficial...by ShadowOne333 96 -
16K views
TheFloW releases new PPPwn kernel exploit for PS4, works on firmware 11.00
TheFlow has done it again--a new kernel exploit has been released for PlayStation 4 consoles. This latest exploit is called PPPwn, and works on PlayStation 4 systems... -
14K views
Nintendo takes down Gmod content from Steam's Workshop
Nintendo might just as well be a law firm more than a videogame company at this point in time, since they have yet again issued their now almost trademarked usual...by ShadowOne333 113 -
13K views
A prototype of the original "The Legend of Zelda" for NES has been found and preserved
Another video game prototype has been found and preserved, and this time, it's none other than the game that spawned an entire franchise beloved by many, the very...by ShadowOne333 31 -
11K views
Anbernic reveals specs details of pocket-sized RG28XX retro handheld
Anbernic is back with yet another retro handheld device. The upcoming RG28XX is another console sporting the quad-core H700 chip of the company's recent RG35XX 2024... -
10K views
Nintendo Switch Online adds two more Nintendo 64 titles to its classic library
Two classic titles join the Nintendo Switch Online Expansion Pack game lineup. Available starting April 24th will be the motorcycle racing game Extreme G and another... -
10K views
Nintendo "Indie World" stream announced for April 17th, 2024
Nintendo has recently announced through their social media accounts that a new Indie World stream will be airing tomorrow, scheduled for April 17th, 2024 at 7 a.m. PT...by ShadowOne333 53
-
-
-
179 replies
Wii U and 3DS online services shutting down today, but Pretendo is here to save the day
Today, April 8th, 2024, at 4PM PT, marks the day in which Nintendo permanently ends support for both the 3DS and the Wii U online services, which include co-op play...by ShadowOne333 -
113 replies
Nintendo takes down Gmod content from Steam's Workshop
Nintendo might just as well be a law firm more than a videogame company at this point in time, since they have yet again issued their now almost trademarked usual...by ShadowOne333 -
98 replies
Nintendo officially confirms Switch successor console, announces Nintendo Direct for next month
While rumors had been floating about rampantly as to the future plans of Nintendo, the President of the company, Shuntaro Furukawa, made a brief statement confirming...by Chary -
97 replies
The first retro emulator hits Apple's App Store, but you should probably avoid it
With Apple having recently updated their guidelines for the App Store, iOS users have been left to speculate on specific wording and whether retro emulators as we...by Scarlet -
96 replies
Delta emulator now available on the App Store for iOS
The time has finally come, and after many, many years (if not decades) of Apple users having to side load emulator apps into their iOS devices through unofficial...by ShadowOne333 -
81 replies
Nintendo Switch firmware update 18.0.1 has been released
A new Nintendo Switch firmware update is here. System software version 18.0.1 has been released. This update offers the typical stability features as all other...by Chary -
80 replies
TheFloW releases new PPPwn kernel exploit for PS4, works on firmware 11.00
TheFlow has done it again--a new kernel exploit has been released for PlayStation 4 consoles. This latest exploit is called PPPwn, and works on PlayStation 4 systems...by Chary -
67 replies
DOOM has been ported to the retro game console in Persona 5 Royal
DOOM is well-known for being ported to basically every device with some kind of input, and that list now includes the old retro game console in Persona 5 Royal...by relauby -
55 replies
Nintendo Switch Online adds two more Nintendo 64 titles to its classic library
Two classic titles join the Nintendo Switch Online Expansion Pack game lineup. Available starting April 24th will be the motorcycle racing game Extreme G and another...by Chary -
53 replies
Nintendo "Indie World" stream announced for April 17th, 2024
Nintendo has recently announced through their social media accounts that a new Indie World stream will be airing tomorrow, scheduled for April 17th, 2024 at 7 a.m. PT...by ShadowOne333
-
Popular threads in this forum
General chit-chat
-
 K3Nv2
Loading…
K3Nv2
Loading… -
 BigOnYa
Loading…
BigOnYa
Loading… -
 Psionic Roshambo
Loading…
Psionic Roshambo
Loading… -
 AncientBoi
Loading…
AncientBoi
Loading…
-
-
-
-
-
-
-
-
-
 @
BakerMan:
why tf do people hate android users? is it the video quality? just because "AnDrOiD = pOoR" bc they don't cost an arm and a leg like iphones do?+1
@
BakerMan:
why tf do people hate android users? is it the video quality? just because "AnDrOiD = pOoR" bc they don't cost an arm and a leg like iphones do?+1 -
 @
BakerMan:
i won't be turned off by an iphone, but don't pick on me for having an android, that's just how this shit should work
@
BakerMan:
i won't be turned off by an iphone, but don't pick on me for having an android, that's just how this shit should work -
-
 @
BigOnYa:
I've owned both iPhone and Androids over the years. Both are just as good, other than Apples higher price. I'm currently on Android, Samsung S21 I think, and very happy with it.
@
BigOnYa:
I've owned both iPhone and Androids over the years. Both are just as good, other than Apples higher price. I'm currently on Android, Samsung S21 I think, and very happy with it. -
-
-
-
-
-
 @
K3Nv2:
Your mind gets in a werid pattern of just finishing then when you're done you're like I need a soda
@
K3Nv2:
Your mind gets in a werid pattern of just finishing then when you're done you're like I need a soda -
-
-
-
-
-
-








