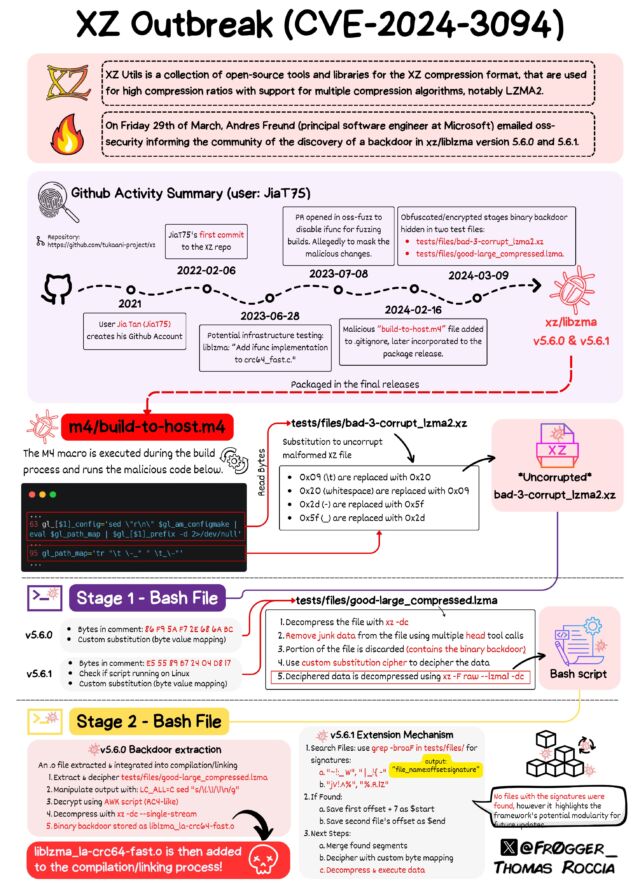
A backdoor was found in Linux most used compression library: liblzma, affecting the SSH Server service (sshd).
https://www.wired.com/story/jia-tan-xz-backdoor/
https://boehs.org/node/everything-i-know-about-the-xz-backdoor
https://nvd.nist.gov/vuln/detail/CVE-2024-3094
You can check if you are running SSH server by running:
If it reports itself as being active, then check for the `xz` version:
If it reports itself being 5.6.0 or 5.6.1, you machine was most likely compromised. Update it **immediately** .
https://www.wired.com/story/jia-tan-xz-backdoor/
https://boehs.org/node/everything-i-know-about-the-xz-backdoor
https://nvd.nist.gov/vuln/detail/CVE-2024-3094
You can check if you are running SSH server by running:
systemctl status sshdIf it reports itself as being active, then check for the `xz` version:
$ xz --versionIf it reports itself being 5.6.0 or 5.6.1, you machine was most likely compromised. Update it **immediately** .