Incognito_RCM - wipe personal information to reduce risk of ban
Incognito_RCM
since Incognito by blawar doesn't work on vanilla atmosphere, I made a payload to use with hekate (or any other payload injector) with the same functionality.
Incognito_RCM wipes personal information from your Nintendo Switch by removing it from prodinfo.
Functionality:
since Incognito by blawar doesn't work on vanilla atmosphere, I made a payload to use with hekate (or any other payload injector) with the same functionality.
Incognito_RCM wipes personal information from your Nintendo Switch by removing it from prodinfo.
Functionality:
- wipe personal information on sysnand/emunand
- backup prodinfo from sysnand/emunand
- restore prodinfo to sysnand/emunand
Since NAND memory is encrypted, this is based on shchmue's Lockpick_RCM to first get the neccessary encryption keys.
You can apply Incognito_RCM directly after installing atmosphere or any time after and it has the advantage that you don't need to set 90DNS after an internet connection and possibly communication with nintendo servers is already established. (You can apply 90DNS anyway)
This has only been tested by me on firmware 8.1.0, so please test it and report back.
Since it has only been tested by me, keep a hekate nand backup ready to be safe.
source: https://github.com/jimzrt/Incognito_RCM
releases: https://github.com/jimzrt/Incognito_RCM/releases
Disclaimer:
This is early stage and there is no guarantee that everything works as expected! Please have a hekate NAND backup ready!
You can apply Incognito_RCM directly after installing atmosphere or any time after and it has the advantage that you don't need to set 90DNS after an internet connection and possibly communication with nintendo servers is already established. (You can apply 90DNS anyway)
This has only been tested by me on firmware 8.1.0, so please test it and report back.
Since it has only been tested by me, keep a hekate nand backup ready to be safe.
source: https://github.com/jimzrt/Incognito_RCM
releases: https://github.com/jimzrt/Incognito_RCM/releases
Disclaimer:
This is early stage and there is no guarantee that everything works as expected! Please have a hekate NAND backup ready!
Screenshots:
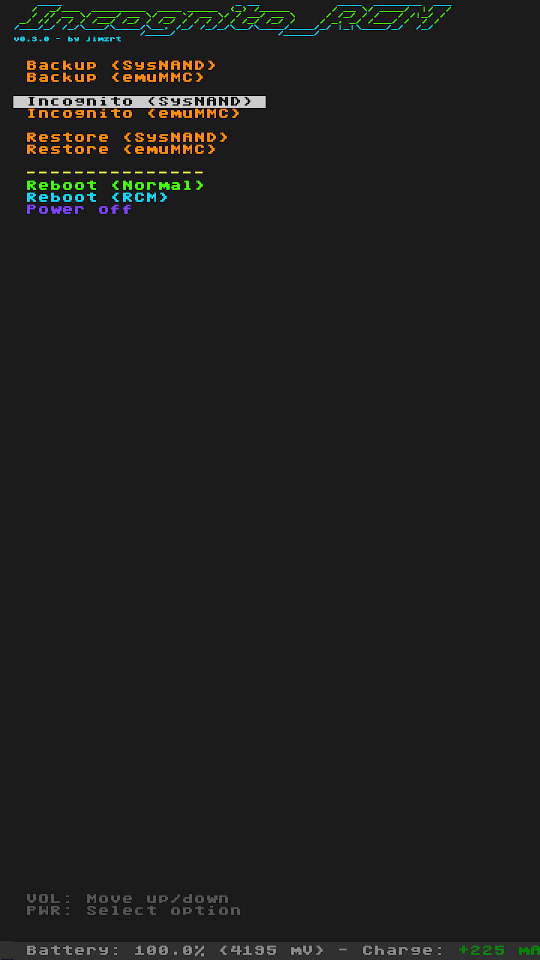
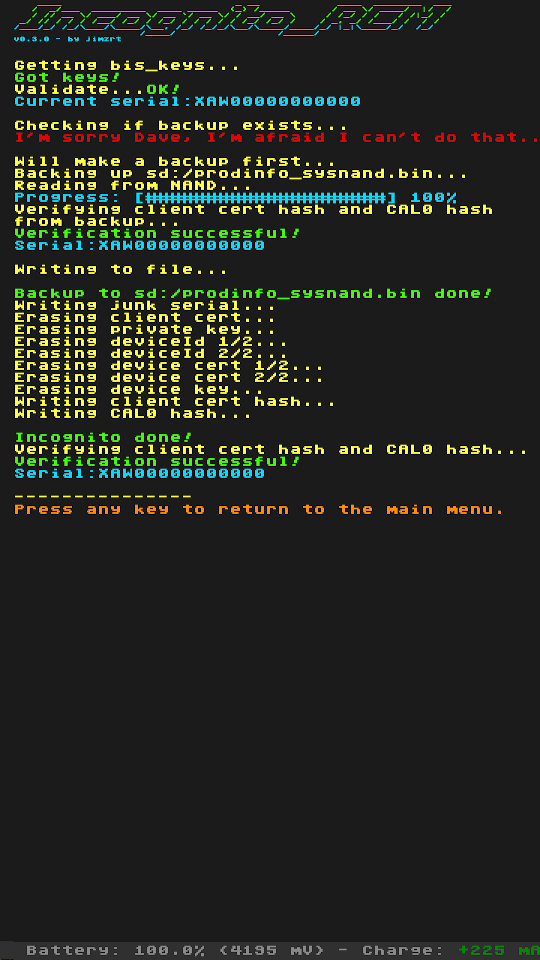
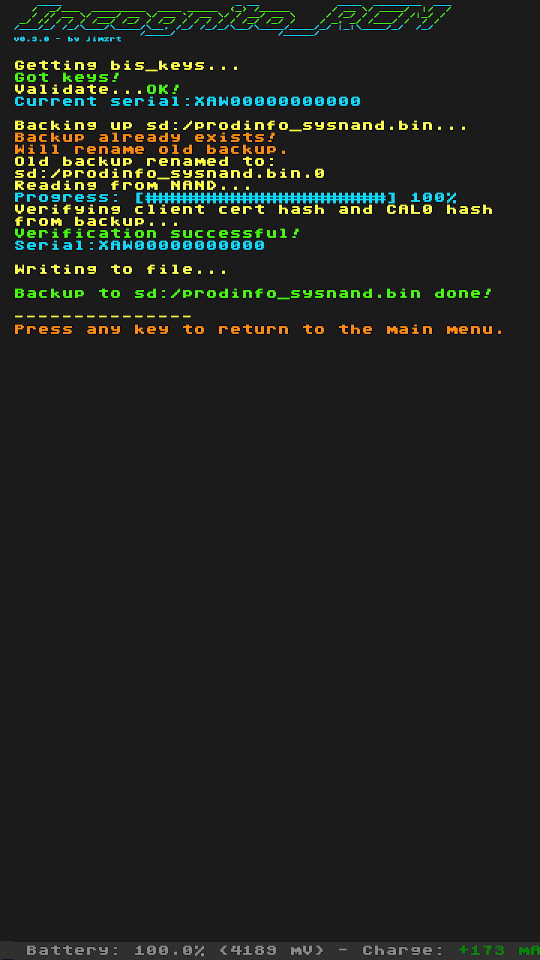
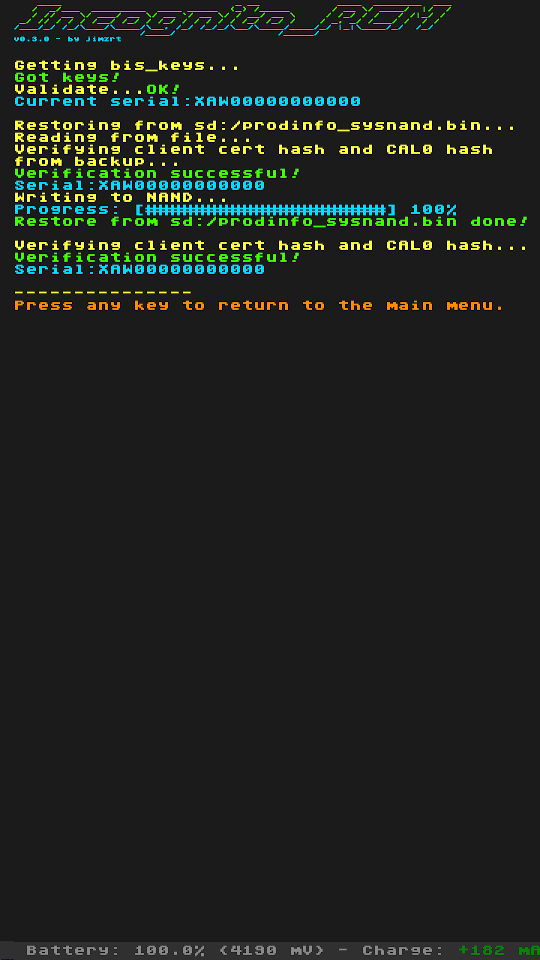
Changelog:
v0.6.1
- bugfix: write to emummc instead of sdmmc
- incorporate hekate & lockpick_rcm changes
- reboot to payload
- firmware 9.1.0 support
- adopt lockpick_rcm and hekate changes (includes fixing of possible bugs and better resource management)
- reduced payload size
- use tui progressbar
- more error handling
- backup validation when reading and writing
- retry up to 5 times when reading and writing before aborting
- more validation
- code cleanup and refactoring
- much faster read and write speed (not sector by sector anymore)
- much more validation and verification (still not perfect)
- more error handling (still not perfect)
- backups aren't overwritten, old backups are renamed
- check for backup before applying incognito
- auto-restore backup if something goes wrong
- Removed external libraries and better handling of reading big chunks of memory.
Last edited by jimzrt,




