Just knee deep into ASM hacking. I share this to spur discussion. This is not a tutorial on ASM hacking.
The game: SHIN MEGAMI TENSEI Ⅴ 1.0.1 TID: 0100B870126CE000 BID: A6A06F3BAEFE4D75
The item I looked at: HP of the combatants
The tools: Atmosphere 1.2.4 with GDB enabled, Edizon se 3.8.25, IDA pro
Refer to release note on edizon se 3.8.25g on enabling GDB.
I use edizon se to search for HP during a combat. Since it is displayed during combat and it is turn base it is very easy to find the memory location. After finding the memory location now it is time to look for how the code that touch this memory looks like.
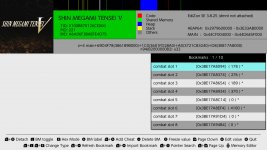
I add the found address as a bookmark. Launch pointer searcher se to download the bookmark. ( You can also just reading it off screen and type it )
Now we need to detach dmnt and make sure nothing is attached to the game. Launch edizon se, press ZL+B to detach dmnt ( and the "no auto attach" setting enabled if you are using profile to launch edizon se ). You should see a screen like this if you use profile to launch edizon se and you must exit this screen by pressing home. If you use hbmenu to launch edizon se just ZL+B will do.
Now with dmnt detached you are ready to ask GDB to attach to the game.
On the PC side launch IDA pro without loading anything.
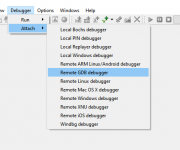
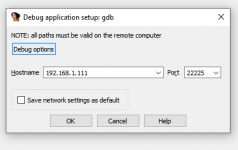
put in the IP address of your switch and port 22225. In Debug options you need to specify ARM64
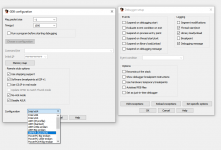
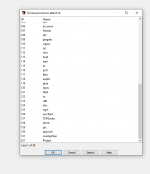
Identify the game. It is normally Application but in this case it is Project. You can also note down from edizon se screen above that the PID is 221.
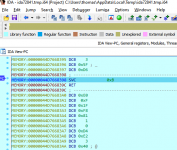
Successfully attached to the game.
Next we need to set a trace watch on the memory.
Press g. Type or paste the address here.
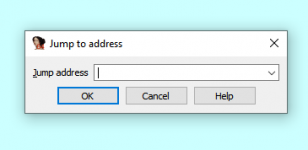
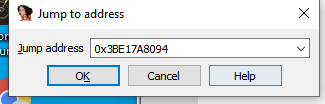
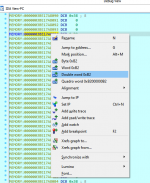
right click and set it to double word
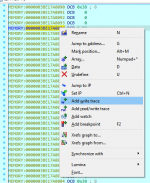
right click and add write trace
press F9 to continue the game
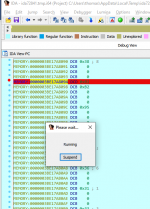
Play the game until HP is being written to. The game will freeze.
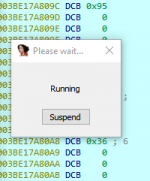
Click on suspend and see where the code is writing to HP.
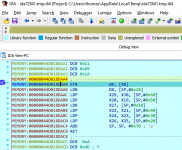
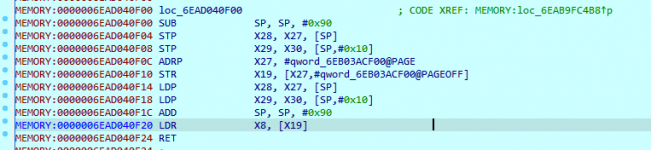
Hover over [X8] and see that it is the memory location.
W9 has the new value.
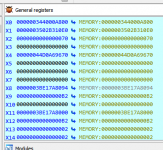
Can be seen in the register windows too.
X9 is the full 64 bit register and W9 is the lower half of X9 with only the lower order 32 bits.
Next look for the start of the sub routine by clicking on address that are 32bit aligned. i.e. ends with 0,4,8,C
Press C to disassemble the code.
This is a trial and error process.
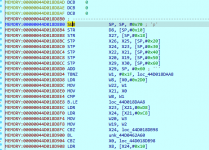
This looks promising, it is preparing the stack.
Press P here
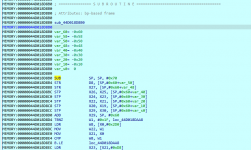
Press F5 and IDA pro try to make C code out of the assembly, let's see whether the code make sense.

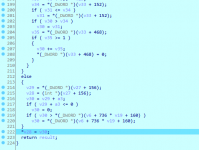
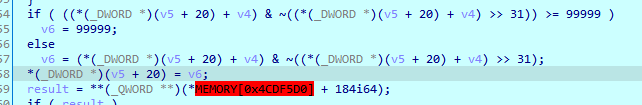
Looks promising, the highlighted line is where we stopped.
*v28 is where the HP is and looks like the lines above are responsible for what is written and where v28 is pointing to.
Unfortunately GDBstub from Atmosphere don't work that well with IDA pro. I am only able to make use of F4 (jump to cursor) and it does not work on the same address subsequently, you have to F4 to another line before you can F4 on this line again.
It is still very useful to explore the code.
First let's check what the two group above do.

Put F4 on the if and observe the result then put F4 on the else and observe the result.
It looks like the top is for HP and the bottom is for MP.
From the code it can be seen that HP is with a offset of 148 0x94 and MP is with a offset of 156 0x98. ( already knew the address of HP and MP by normal edizon se search and can use that information to understand the code )
With F4ing it can be seen that this code walk through the whole party engaged in combat.
Next look for what code change v27. Click on v27 and look for code that modify it. In this case it is line 189 and it hints at the memory block of each participant in the combat is offset by 0x2E0.

Detach to be able to use Edizon se and other tools.
Switch between dmnt and GDB as often as you like.
If IDA pro looks like it is going crazy due to GDB incompatibility quickly detach or risk a switch crash.
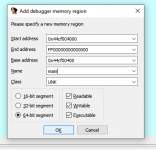
Create a manual memory region to get offset display relative to main.
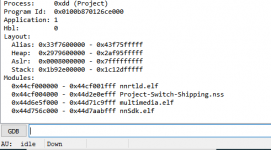
Type get info, you can also use edizon se for this information, but this you can cut and paste so it is easier.
Thanks for reading.
Special thanks to Eiffel2018 from whom I learned most of what is written here.
For more advanced topic check out this thread https://gbatemp.net/threads/atmospheres-gdb.602435/
The game: SHIN MEGAMI TENSEI Ⅴ 1.0.1 TID: 0100B870126CE000 BID: A6A06F3BAEFE4D75
The item I looked at: HP of the combatants
The tools: Atmosphere 1.2.4 with GDB enabled, Edizon se 3.8.25, IDA pro
Refer to release note on edizon se 3.8.25g on enabling GDB.
I use edizon se to search for HP during a combat. Since it is displayed during combat and it is turn base it is very easy to find the memory location. After finding the memory location now it is time to look for how the code that touch this memory looks like.
I add the found address as a bookmark. Launch pointer searcher se to download the bookmark. ( You can also just reading it off screen and type it )
Now we need to detach dmnt and make sure nothing is attached to the game. Launch edizon se, press ZL+B to detach dmnt ( and the "no auto attach" setting enabled if you are using profile to launch edizon se ). You should see a screen like this if you use profile to launch edizon se and you must exit this screen by pressing home. If you use hbmenu to launch edizon se just ZL+B will do.

Now with dmnt detached you are ready to ask GDB to attach to the game.
On the PC side launch IDA pro without loading anything.


put in the IP address of your switch and port 22225. In Debug options you need to specify ARM64


Identify the game. It is normally Application but in this case it is Project. You can also note down from edizon se screen above that the PID is 221.

Successfully attached to the game.
Next we need to set a trace watch on the memory.
Press g. Type or paste the address here.




right click and set it to double word

right click and add write trace
press F9 to continue the game

Play the game until HP is being written to. The game will freeze.

Click on suspend and see where the code is writing to HP.

Hover over [X8] and see that it is the memory location.
W9 has the new value.

Can be seen in the register windows too.
X9 is the full 64 bit register and W9 is the lower half of X9 with only the lower order 32 bits.
Next look for the start of the sub routine by clicking on address that are 32bit aligned. i.e. ends with 0,4,8,C
Press C to disassemble the code.
This is a trial and error process.

This looks promising, it is preparing the stack.
Press P here

Press F5 and IDA pro try to make C code out of the assembly, let's see whether the code make sense.


Looks promising, the highlighted line is where we stopped.
*v28 is where the HP is and looks like the lines above are responsible for what is written and where v28 is pointing to.
Unfortunately GDBstub from Atmosphere don't work that well with IDA pro. I am only able to make use of F4 (jump to cursor) and it does not work on the same address subsequently, you have to F4 to another line before you can F4 on this line again.
It is still very useful to explore the code.
First let's check what the two group above do.

Put F4 on the if and observe the result then put F4 on the else and observe the result.
It looks like the top is for HP and the bottom is for MP.
From the code it can be seen that HP is with a offset of 148 0x94 and MP is with a offset of 156 0x98. ( already knew the address of HP and MP by normal edizon se search and can use that information to understand the code )
With F4ing it can be seen that this code walk through the whole party engaged in combat.
Next look for what code change v27. Click on v27 and look for code that modify it. In this case it is line 189 and it hints at the memory block of each participant in the combat is offset by 0x2E0.

Detach to be able to use Edizon se and other tools.

Switch between dmnt and GDB as often as you like.
If IDA pro looks like it is going crazy due to GDB incompatibility quickly detach or risk a switch crash.

Create a manual memory region to get offset display relative to main.
Type get info, you can also use edizon se for this information, but this you can cut and paste so it is easier.



Thanks for reading.
Special thanks to Eiffel2018 from whom I learned most of what is written here.
For more advanced topic check out this thread https://gbatemp.net/threads/atmospheres-gdb.602435/
Last edited by TomSwitch,