Short Backstory: I bought a Switch from ebay with good serial. The seller told me that after an update the switch won't boot anymore(to my knowledge he didn't put cfw on it). After I got the switch I turned it on and the nintendo logo appeard but after that just blackscreen. After pressing the power button for about 20 seconds to shut it down I tried to boot into hekate which worked and dumped all the stuff and made boot and emmc backup.
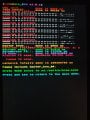
My first problem was dumping the keys via Lockpick_RCM. I get 6 errors for keyblob 0 through 5. I don't know if this is a significant problem but I nevertheless got 78 keys which include tsec_key and secure_boot_key which are used to generate the bis keys.
Also biskeydump only dumps the 3 keys: HWI, SBK and TSEC KEY. No individual bis keys.
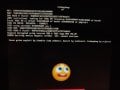
I am currently follow this guide: https://switch.homebrew.guide/usingcfw/manualchoiupgrade to try to restore it to 4.1.0 to get ChoiDujourNX to upgrade it back to 9.1.0 (11 fuses are burnt, so I think that means 9.1.0) but now I am at the point where I need to access the emmc via memloader and HacDiskMount and none of my Bis Keys work.
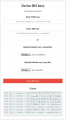
I used this website https://sdsetup.com/biskeygen to get my bis keysbut here is the funny part is that i get different keys when I use tsec and sbk or fuse_cached.bin and tsec_keys.bin but if i use the bin files the tsec and sbk fiels are populated with the same keys as provided earlier. This only happens if I use the keys from prod.keys which have lower case letters in them but are otherwise the same as the ones I got from biskeydump. This is an error on the website which I already submitted a new issue for: https://github.com/noahc3/SDSetup/issues/146
TL;DR
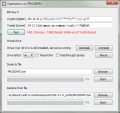
My dumped TSEC and SBK keys (or fuse_cached.bin and tsec_keys.bin files) don't generate the correct BIS keys which I need to decrypt the emmc in HacDiskMount.
My first problem was dumping the keys via Lockpick_RCM. I get 6 errors for keyblob 0 through 5. I don't know if this is a significant problem but I nevertheless got 78 keys which include tsec_key and secure_boot_key which are used to generate the bis keys.

Also biskeydump only dumps the 3 keys: HWI, SBK and TSEC KEY. No individual bis keys.

I am currently follow this guide: https://switch.homebrew.guide/usingcfw/manualchoiupgrade to try to restore it to 4.1.0 to get ChoiDujourNX to upgrade it back to 9.1.0 (11 fuses are burnt, so I think that means 9.1.0) but now I am at the point where I need to access the emmc via memloader and HacDiskMount and none of my Bis Keys work.
I used this website https://sdsetup.com/biskeygen to get my bis keys
TL;DR
My dumped TSEC and SBK keys (or fuse_cached.bin and tsec_keys.bin files) don't generate the correct BIS keys which I need to decrypt the emmc in HacDiskMount.


Last edited by Toby4213,





