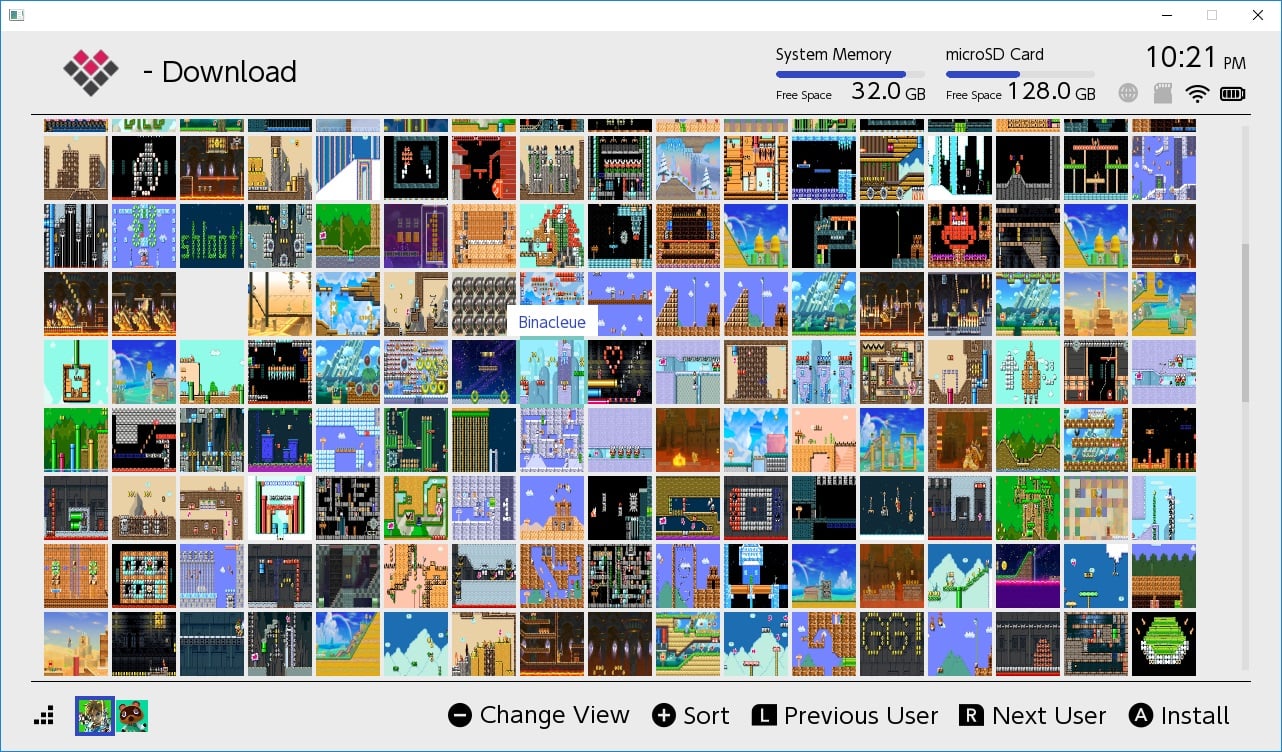
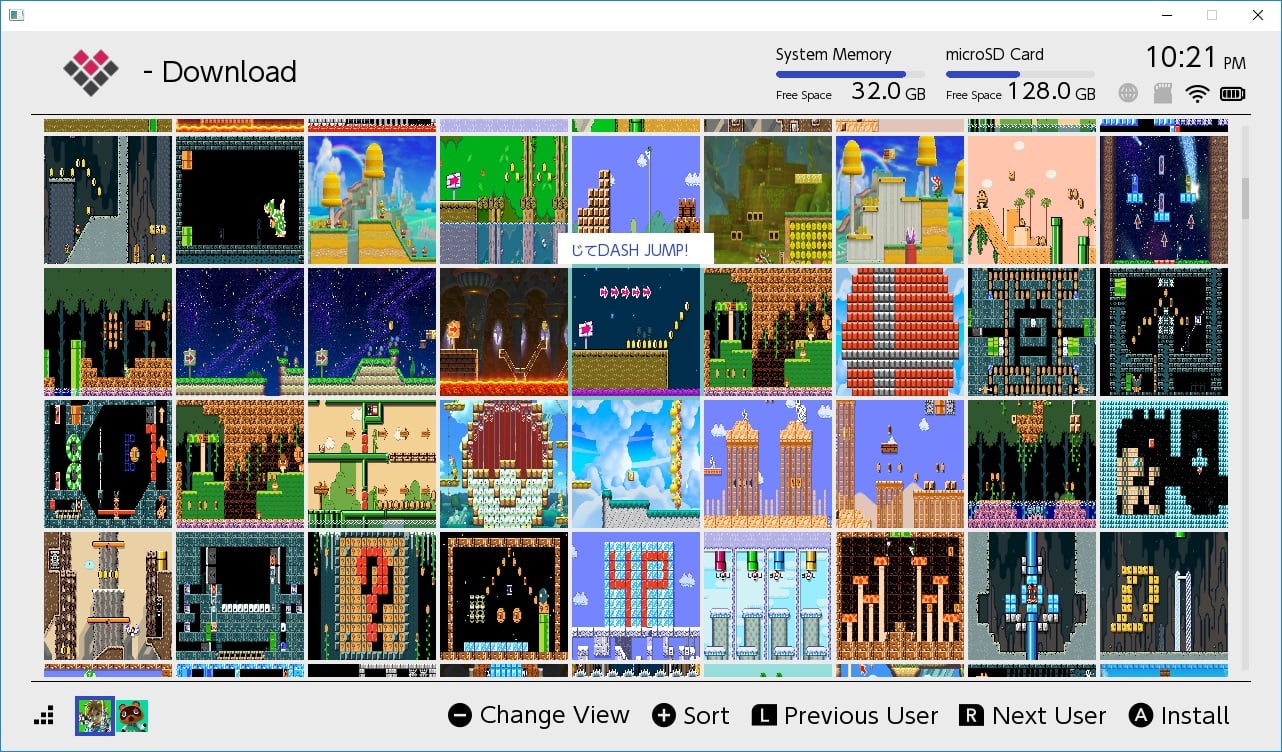
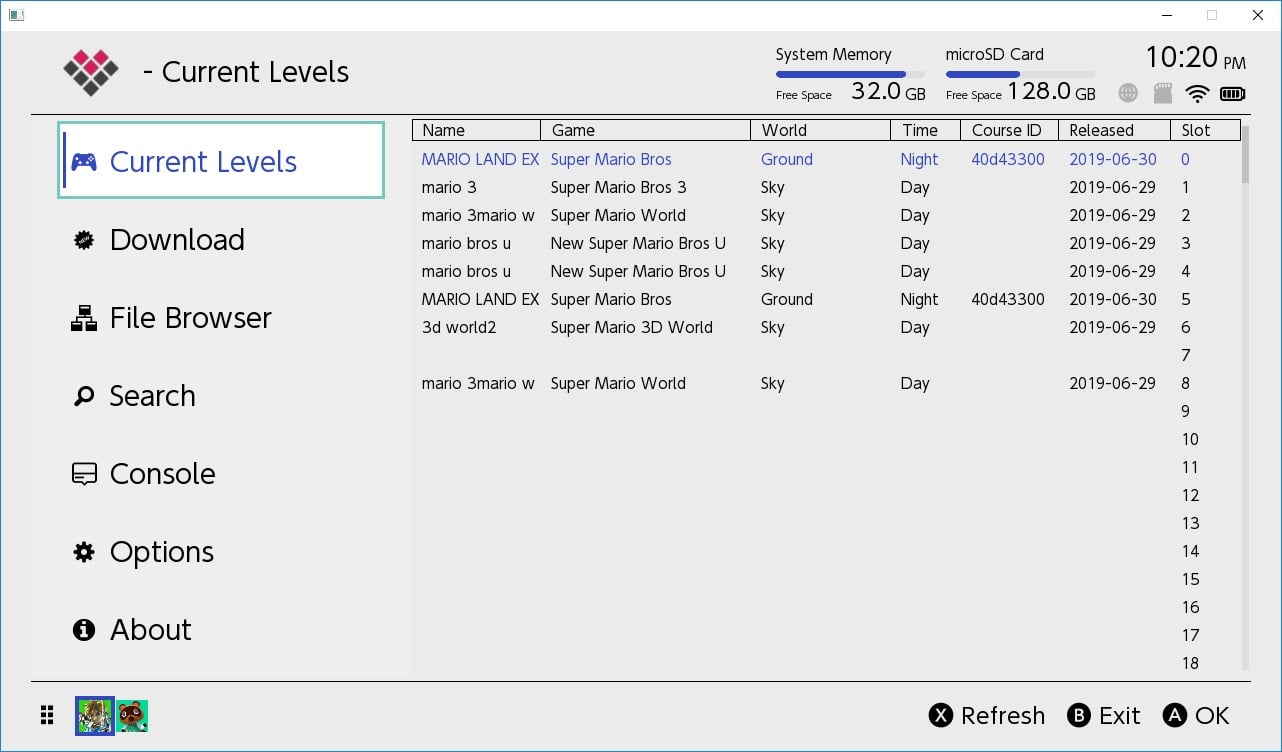
MM-LINX - Super Mario Maker 2 Level Injector
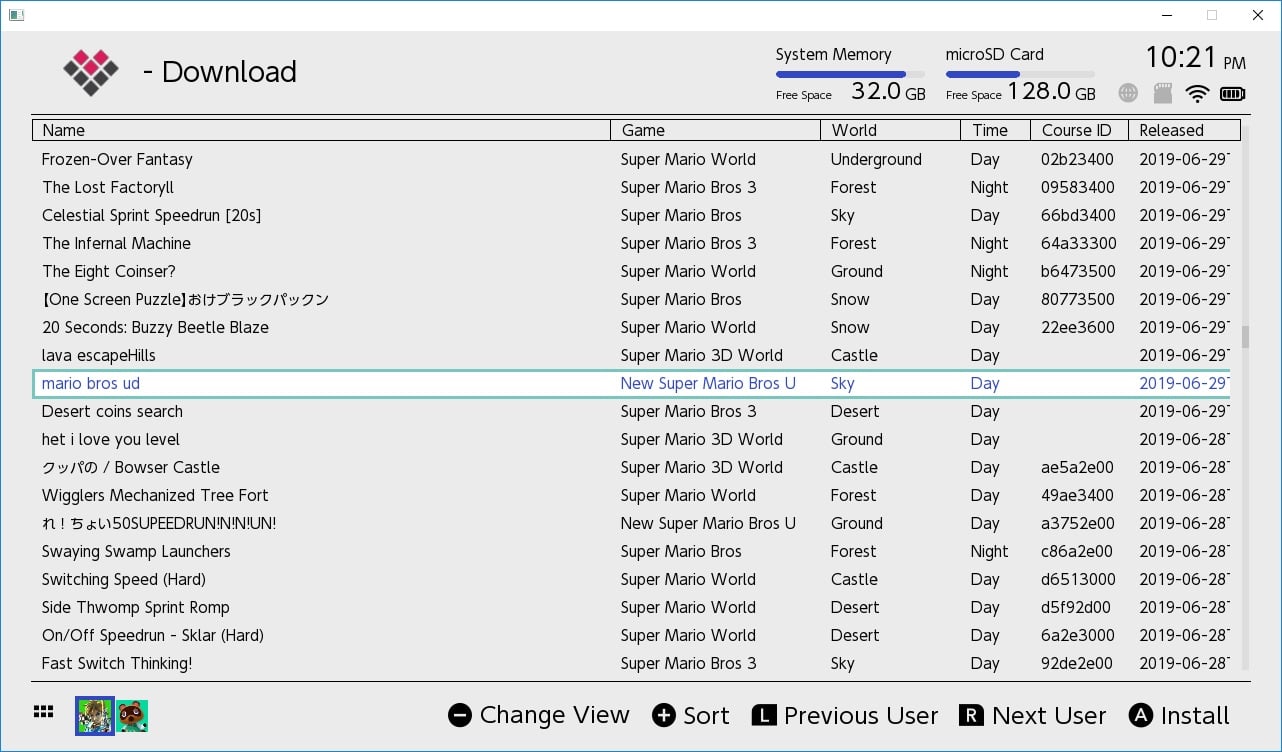
nstall the MM-LINX homebrew application on your switch, to install levels uploaded to https://tinfoil.io/MarioMaker/ directly to your Super Mario Maker 2 Level slots!
Very early release, please be patient and it will get better with time as all of my applications do Feel free to post feature requests and bug reports.
Feel free to post feature requests and bug reports.
This is currently hard coded to use the first user profile. Please ensure that Super Mario Maker 2 is not running, and that you have at least one SMM2 save on the first user's profile.
For maximum compatibility and stability, we recommend that you use ReiNX or SX.
Download: https://github.com/blawar/mmlinx
edit: 1.01 fixed sorting, press + to sort
edit: 1.02 added support for uploading your levels to tinfoil.io from MM-LINX
edit: 1.03 added file browser for installing levels from (sd, ftp, http, gdrive, usb, etc), search, ability to change user, translation (needs work), ability to copy files to and from smm2's save directly, themes, other stuff I probably forgot.
edit: 1.04 saving / loading is now much faster and does not overwrite your save progress; added columns for difficulty, rating, and course id; ability to unlock hammer and super flower on supported cfw's.
edit: 1.05 increased security, mandatory update. Cloud servers will no longer work with previous versions (downloads section will be empty).
Download: https://github.com/blawar/mmlinx
Very early release, please be patient and it will get better with time as all of my applications do
This is currently hard coded to use the first user profile. Please ensure that Super Mario Maker 2 is not running, and that you have at least one SMM2 save on the first user's profile.
For maximum compatibility and stability, we recommend that you use ReiNX or SX.
Download: https://github.com/blawar/mmlinx
edit: 1.01 fixed sorting, press + to sort
edit: 1.02 added support for uploading your levels to tinfoil.io from MM-LINX
edit: 1.03 added file browser for installing levels from (sd, ftp, http, gdrive, usb, etc), search, ability to change user, translation (needs work), ability to copy files to and from smm2's save directly, themes, other stuff I probably forgot.
edit: 1.04 saving / loading is now much faster and does not overwrite your save progress; added columns for difficulty, rating, and course id; ability to unlock hammer and super flower on supported cfw's.
edit: 1.05 increased security, mandatory update. Cloud servers will no longer work with previous versions (downloads section will be empty).
Download: https://github.com/blawar/mmlinx
Attachments
Last edited by blawar,