Tutorial
Updated
Photo guide to installing DSiWare backups on real hardware and emulator
First, some USEFUL NOTES
Tickets are not actually required by the DSi launcher (this was unknown at the time the above procedure was written), you may skip the related steps
While still incomplete, @MarioMasta64 is working on automating this process for Windows+Python users:
http://gbatemp.net/threads/a-tool-to-make-converting-dsiware-from-3ds-to-dsi-easier.479996/
If you are using an emunand (through Hiya, for example), consider using DSi Title Manager instead; there's no reason it couldn't work on sysnand with minor changes but... it doesn't do that, yet or ever
Steal Acquire some decrypted DSiware apps. You can use Funkeycia, 3DSeStuff, etc the 3DS eShop to legally download them, rip them to cia, then use ctrtool to extract the cia into "contents" = .app (the very newest versions of ctrtool decrypt them during this extraction); alternatively you can use Godmode9 to directly copy the appropriate .app under twln:/title/00030004/* to the SD.
There's also a no-intro catalogue but no romset I know of, officer...
Backup your console's NAND, CID, and ConsoleID using well documented methods (hardmod if you have some DSiware that can be copied to SD, or fwTool+safety mod if you have an usable DSiware exploit - Team Twiizer's original sudokuhax is not suitable #clobberedkeyslots, while fourswordshax and the leaked ugopwn use minitwlpayload).
If you're using NO$GBA with a nand you didn't dump yourself, you can find the CID and the byteswapped ConsoleID by looking at the end of the dump with a hex editor.

(Adding this block is also how you convert a raw backup for use with NO$GBA, just in case you didn't read the manual)
Use TwlTool to decrypt the nand.

Mount the 1st partition of the decrypted image with OSFMount (Linux equivalent: losetup + mount; Mac equivalent, hdiutil + mount I guess?).
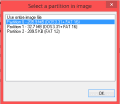
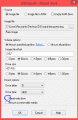
Pick (any?) ticket from the NAND, preferably from the regular DSiware category = 00030004, and decrypt it with TwlTool. This will be a base for the edited tickets we will make.
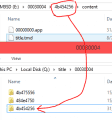
Open the folder with our dumped title. You will find a "content" folder, possibly a "data" folder, and a .ctx file if it came from a 3DS.
Delete it, then go to the content folder.
Remove the "cmd" folder, and the 3DS-format TMD.
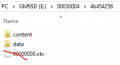
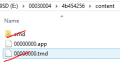
Search the TMD pack for the full TitleID of the DSiware; copy the TMD to the content folder, renaming it to "title.tmd".
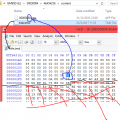
Open title.tmd in a hex editor.

Find offset 1E7; rename the .app file (better known as .srl or .nds) so that the last 2 digits are the ones written at 1E7.
Find offset 208; delete everything from there to the end of the file. (A small number of tmds are already trimmed).
Save the file.
Open the ticket we decrypted earlier in a hex editor.
Find offset 1DC and replace the next 8 bytes with the TitleID of the app we're installing;
Save the file with a name equal to the TitleID-low of the app.

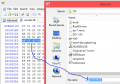
Use TwlTool to encrypt the ticket, and put it into the NAND.
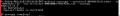
Copy the title's (content & data) folder to the NAND.
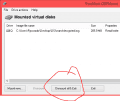
Unmount the NAND and re-encrypt it.

If you're using NO$GBA, you will have to re-add the footer since it will have been removed by TwlTool's NAND features.

Enjoy your DSiWarez, and if you liked it, BUY THE ORIGINAL... oh wait, they closed the DSi shop


Tickets are not actually required by the DSi launcher (this was unknown at the time the above procedure was written), you may skip the related steps
While still incomplete, @MarioMasta64 is working on automating this process for Windows+Python users:
http://gbatemp.net/threads/a-tool-to-make-converting-dsiware-from-3ds-to-dsi-easier.479996/
If you are using an emunand (through Hiya, for example), consider using DSi Title Manager instead; there's no reason it couldn't work on sysnand with minor changes but... it doesn't do that, yet or ever
There's also a no-intro catalogue but no romset I know of, officer...
Backup your console's NAND, CID, and ConsoleID using well documented methods (hardmod if you have some DSiware that can be copied to SD, or fwTool+safety mod if you have an usable DSiware exploit - Team Twiizer's original sudokuhax is not suitable #clobberedkeyslots, while fourswordshax and the leaked ugopwn use minitwlpayload).
If you're using NO$GBA with a nand you didn't dump yourself, you can find the CID and the byteswapped ConsoleID by looking at the end of the dump with a hex editor.
(Adding this block is also how you convert a raw backup for use with NO$GBA, just in case you didn't read the manual)
Use TwlTool to decrypt the nand.

Mount the 1st partition of the decrypted image with OSFMount (Linux equivalent: losetup + mount; Mac equivalent, hdiutil + mount I guess?).


Pick (any?) ticket from the NAND, preferably from the regular DSiware category = 00030004, and decrypt it with TwlTool. This will be a base for the edited tickets we will make.
Open the folder with our dumped title. You will find a "content" folder, possibly a "data" folder, and a .ctx file if it came from a 3DS.
Delete it, then go to the content folder.
Remove the "cmd" folder, and the 3DS-format TMD.


Search the TMD pack for the full TitleID of the DSiware; copy the TMD to the content folder, renaming it to "title.tmd".
Open title.tmd in a hex editor.

Find offset 1E7; rename the .app file (better known as .srl or .nds) so that the last 2 digits are the ones written at 1E7.
Find offset 208; delete everything from there to the end of the file. (A small number of tmds are already trimmed).
Save the file.

Open the ticket we decrypted earlier in a hex editor.
Find offset 1DC and replace the next 8 bytes with the TitleID of the app we're installing;
Save the file with a name equal to the TitleID-low of the app.


Use TwlTool to encrypt the ticket, and put it into the NAND.
Copy the title's (content & data) folder to the NAND.

Unmount the NAND and re-encrypt it.


If you're using NO$GBA, you will have to re-add the footer since it will have been removed by TwlTool's NAND features.
Enjoy your DSiWarez, and if you liked it, BUY THE ORIGINAL... oh wait, they closed the DSi shop


Last edited by Ryccardo,









