TWLTOOL: DSi Research and Hacking Multitool
Hey all! Here's the newest thing I've been working on. TWLTool is the culmination of a ton of research into the DSi (TWL) platform,
initially started on the 3DS (TWL_FIRM) and eventually moved over to real hardware.
TWLTool has a good handful of features, most of which are brand new for public tools:
NAND decryption/re-encryption
Given only a consoleID (obtainable from any DSi export) and NAND CID (available from certain SD readers or included savegame hax)
you can now completely decrypt and modify your DSi's NAND contents! This is useful for a ton of things, see below.
SRL de/encryption
Allows decrypting of the DSi-specific regions of DSi-exclusive and enhanced games/titles.
boot2 decryption
Decrypts the second-stage bootloader directly from a DSi NAND image, or from a TWL_FIRM boot2 image. This will output an arm7.bin
and arm9.bin, ready for whatever analysis you want.
More!
eventually.
Guides and such
Basic NAND decryption
Title downgrading
Re-enable classic DSiWarehax installation by downgrading System Settings
Direct DSiWarehax injection (without settings downgrade)
Flashcart re-enabling
Downgrading the flashcart whitelist and/or menu will re-enable previously-blocked DSi-compatible flashcarts.
More!
The sheer shittiness of my eMMC reading/writing setup means I haven't fully explored all the possibilities of my own tool. There's
certainly a ton more possible, if you're willing to dig a bit.
SPECIAL THANKS
Martin Korth, for the invaluable documentation on his resource GBATEK (http://problemkaputt.de/gbatek.htm). I wouldn't have been inspired to make this tool without having seen all his documentation on the system.
CaitSith2, for the source to his tool dsi_srl_extractor. The DSi-oriented crypto libs from that program drive this one, and this program wouldn't have been possible without such a robust backend.
Team Twiizers, for the actual savegame hax which drove me to build nand crypto tools.
Yellows8, for occasionally dropping hints in random corners of the internet over the last 6 years, as well as (vaguely related) all his 3DS documentation. "Hey ninty/someone with sd_key."
Neimod and 3DSGuy, for making CTRTOOL. I borrow some utils and such from there.
Dazzozo and Shiny Quagsire; for moral support, tons of help with documentation, and salt.
Changelog:
DOWNLOADS - v1.6, 5/25/2016
For the sake of making sure this tool stays available, I've both attached it to this post and made it available on Mega and Mediafire.
MEGA
MEDIAFIRE
Hey all! Here's the newest thing I've been working on. TWLTool is the culmination of a ton of research into the DSi (TWL) platform,
initially started on the 3DS (TWL_FIRM) and eventually moved over to real hardware.
TWLTool has a good handful of features, most of which are brand new for public tools:
NAND decryption/re-encryption
Given only a consoleID (obtainable from any DSi export) and NAND CID (available from certain SD readers or included savegame hax)
you can now completely decrypt and modify your DSi's NAND contents! This is useful for a ton of things, see below.
SRL de/encryption
Allows decrypting of the DSi-specific regions of DSi-exclusive and enhanced games/titles.
boot2 decryption
Decrypts the second-stage bootloader directly from a DSi NAND image, or from a TWL_FIRM boot2 image. This will output an arm7.bin
and arm9.bin, ready for whatever analysis you want.
More!
eventually.
Guides and such
Basic NAND decryption
DSi NAND images can be dumped with the following hardware pinouts (also available in the release zips):
DSi:
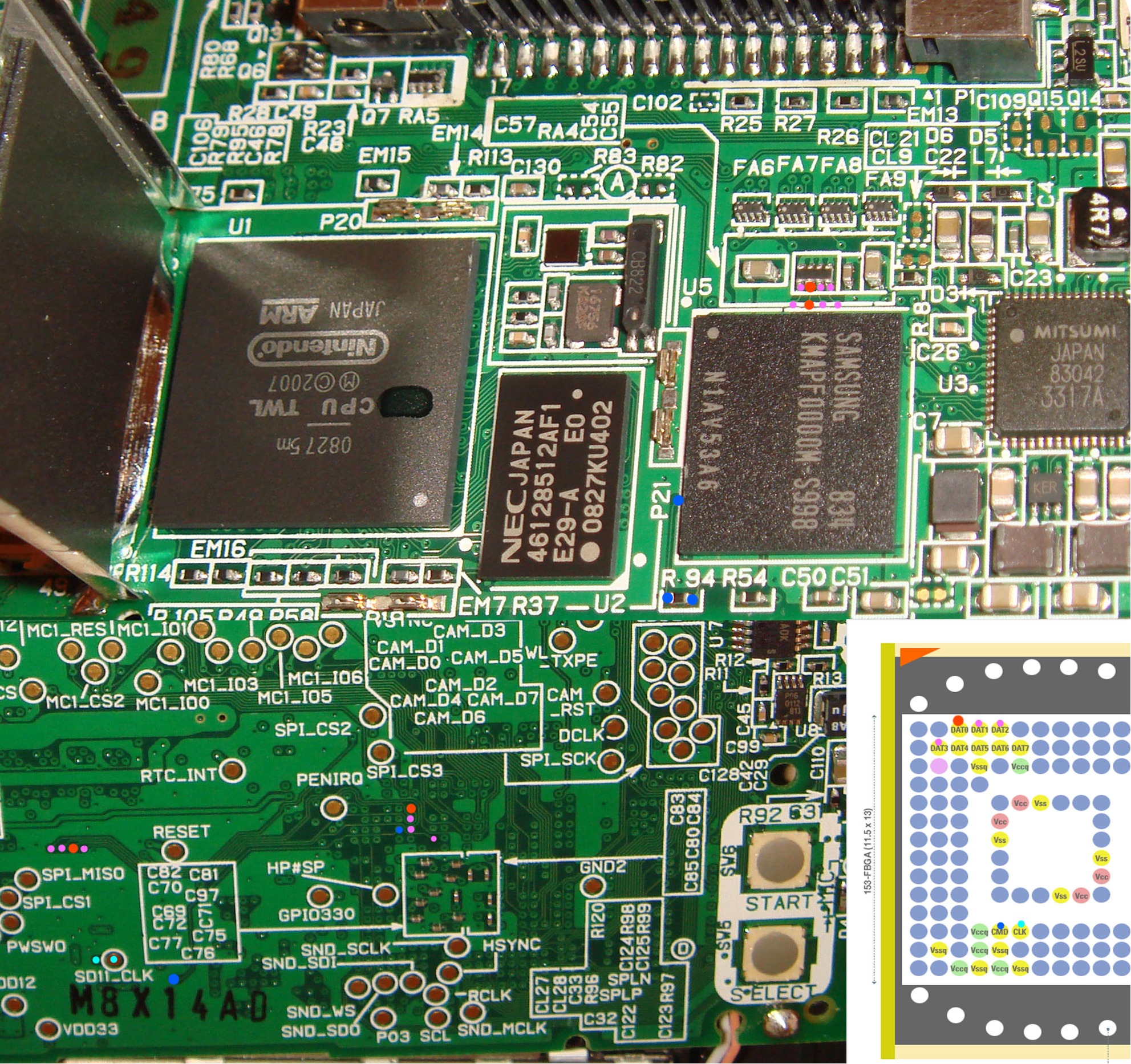
DSi XL:

Tools such as Win32DiskImager (http://sourceforge.net/projects/win32diskimager/) can be used to read out your image once your setup works. Be sure to make more than one dump and verify!
Once you've got that, you should grab your ConsoleID from a DSiWare export. Simply copy any game to your SD card and use dsi_srl_extractor with the option --basename=[name].
Open [name].footer up in a hex editor and search for 'Root-CA00000001-MS00000008-TW[somenumber]-[anothernumber] .
The number after the dash is your ConsoleID. It'll start with 08201 on DSi, 08202 on rev2 DSi, and 08A20 on DSi XL.
Finally, you'll need to dump your CID from your NAND.
This cannot be done with USB readers, but can be done with low-level SD readers like the Raspberry Pi (If someone can find an easy guide for this I'll link it here) or through a hacked save for the game The Biggest Loser.
To run the hacked save, you'll need some way to restore a savegame onto a cart. This can be done through the Gateway 3DS menu, or SavSender for the original DS. You'll know the save worked if the game boots to a black screen with awful MIDI menu music.
After running the hacked save, dump the savegame off your cart. Your CID will be at 0x800, ready to copy-paste into TWLTool.
Once you've got all of this (and reliable backups!!) usage is simple:
TWLTool nandcrypt --cid [16-byte-long hex cid] --consoleid [8-byte-long consoleID] --in [filename] (--out [filename])
The exact same process is repeated to re-encrypt. Just run your decrypted NAND through the file again.
From this point, you can actually mount your NAND and explore the files on it, as well as pull off a ton of useful hacks. For NAND mounting on Windows, I recommend OSFMount.
DSi:

DSi XL:

Tools such as Win32DiskImager (http://sourceforge.net/projects/win32diskimager/) can be used to read out your image once your setup works. Be sure to make more than one dump and verify!
Once you've got that, you should grab your ConsoleID from a DSiWare export. Simply copy any game to your SD card and use dsi_srl_extractor with the option --basename=[name].
Open [name].footer up in a hex editor and search for 'Root-CA00000001-MS00000008-TW[somenumber]-[anothernumber] .
The number after the dash is your ConsoleID. It'll start with 08201 on DSi, 08202 on rev2 DSi, and 08A20 on DSi XL.
Finally, you'll need to dump your CID from your NAND.
This cannot be done with USB readers, but can be done with low-level SD readers like the Raspberry Pi (If someone can find an easy guide for this I'll link it here) or through a hacked save for the game The Biggest Loser.
To run the hacked save, you'll need some way to restore a savegame onto a cart. This can be done through the Gateway 3DS menu, or SavSender for the original DS. You'll know the save worked if the game boots to a black screen with awful MIDI menu music.
After running the hacked save, dump the savegame off your cart. Your CID will be at 0x800, ready to copy-paste into TWLTool.
Once you've got all of this (and reliable backups!!) usage is simple:
TWLTool nandcrypt --cid [16-byte-long hex cid] --consoleid [8-byte-long consoleID] --in [filename] (--out [filename])
The exact same process is repeated to re-encrypt. Just run your decrypted NAND through the file again.
From this point, you can actually mount your NAND and explore the files on it, as well as pull off a ton of useful hacks. For NAND mounting on Windows, I recommend OSFMount.
Title downgrading
It's possible to downgrade bits and pieces - or your entire system - once you've managed to decrypt your nand. The basic process is as follows:
-Grab title and TMD from NUSDownloader (or elsewhere). Update your database too.
Be sure to decrypt the title! NUSDownloader needs the DSi common key in a file named 'dsikey.bin' to do so.
-Delete the existing title and TMD from the /title folder on your NAND. Replace them with your downloaded ones, being sure to rename the tmd to 'title.tmd'. (do NOT rename the .app!)
-Re-encrypt nand and flash it to your system. Done!
-Grab title and TMD from NUSDownloader (or elsewhere). Update your database too.
Be sure to decrypt the title! NUSDownloader needs the DSi common key in a file named 'dsikey.bin' to do so.
-Delete the existing title and TMD from the /title folder on your NAND. Replace them with your downloaded ones, being sure to rename the tmd to 'title.tmd'. (do NOT rename the .app!)
-Re-encrypt nand and flash it to your system. Done!
Re-enable classic DSiWarehax installation by downgrading System Settings
By downgrading System Settings to v512 (I think!! If I'm wrong, tell me which it actually is and I'll update this), your system will be able to import DSiWare exploits signed by any system.
This will let you run all the old DSiWarehax on any system, even on 1.4.5.
This will let you run all the old DSiWarehax on any system, even on 1.4.5.
Direct DSiWarehax injection (without settings downgrade)
Arguably the better, and more future-proof, option: By injecting one of the included DSiWarehax saves to your NAND, you'll instantly have hax without any dependence on Team Twiizers servers or settings downgrades.
To do so, rename a save to public.sav and move it to the appropriate /title/00030004/xxxxxxxx/data/ folder. Done.
To do so, rename a save to public.sav and move it to the appropriate /title/00030004/xxxxxxxx/data/ folder. Done.
Flashcart re-enabling
Downgrading the flashcart whitelist and/or menu will re-enable previously-blocked DSi-compatible flashcarts.
More!
The sheer shittiness of my eMMC reading/writing setup means I haven't fully explored all the possibilities of my own tool. There's
certainly a ton more possible, if you're willing to dig a bit.
SPECIAL THANKS
Martin Korth, for the invaluable documentation on his resource GBATEK (http://problemkaputt.de/gbatek.htm). I wouldn't have been inspired to make this tool without having seen all his documentation on the system.
CaitSith2, for the source to his tool dsi_srl_extractor. The DSi-oriented crypto libs from that program drive this one, and this program wouldn't have been possible without such a robust backend.
Team Twiizers, for the actual savegame hax which drove me to build nand crypto tools.
Yellows8, for occasionally dropping hints in random corners of the internet over the last 6 years, as well as (vaguely related) all his 3DS documentation. "Hey ninty/someone with sd_key."
Neimod and 3DSGuy, for making CTRTOOL. I borrow some utils and such from there.
Dazzozo and Shiny Quagsire; for moral support, tons of help with documentation, and salt.
Changelog:
v1.6 - 5/25/2016
-CID and consoleID can now be loaded from files (just pass a filename instead of a hex ID)
-TWL decryption now decrypts MBR and partitions (copying the rest) instead of annhilating unencrypted parts
-3DS consoleID bruteforce is slightly faster and supports exporing ID to file on completion
-System file crypto should support 3DS now
v1.5 - 5/23/2016
-Add support for dev.kp, ticket, etc decryption (ES block crypto with system (not TAD) key)
v1.1 - 7/24/2015
-Initial(ish) release
-CID and consoleID can now be loaded from files (just pass a filename instead of a hex ID)
-TWL decryption now decrypts MBR and partitions (copying the rest) instead of annhilating unencrypted parts
-3DS consoleID bruteforce is slightly faster and supports exporing ID to file on completion
-System file crypto should support 3DS now
v1.5 - 5/23/2016
-Add support for dev.kp, ticket, etc decryption (ES block crypto with system (not TAD) key)
v1.1 - 7/24/2015
-Initial(ish) release
DOWNLOADS - v1.6, 5/25/2016
For the sake of making sure this tool stays available, I've both attached it to this post and made it available on Mega and Mediafire.
MEGA
MEDIAFIRE
Attachments
Last edited by WulfyStylez,
, Reason: changelog













